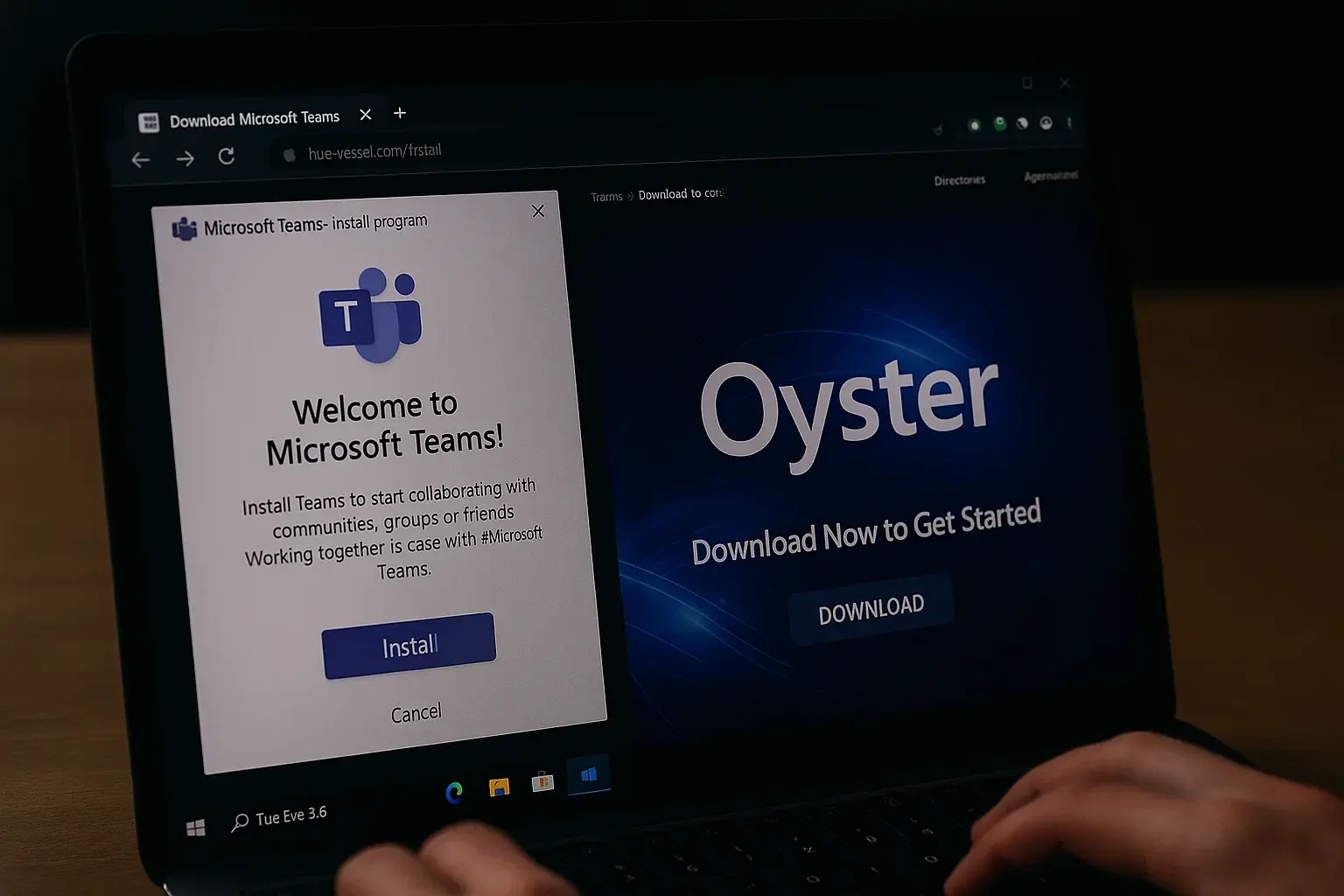
At TecnetOne, we’re issuing an alert about an active campaign in which cybercriminals are using poisoned SEO techniques and paid search ads to distribute fake Microsoft Teams installers. The goal? To infect Windows devices with Oyster, a backdoor-type malware that gives attackers remote and persistent access to corporate networks.
Also known as Broomstick or CleanUpLoader, Oyster was first detected in 2023 and has since been linked to multiple attack campaigns. Once inside the system, it allows hackers to execute commands, deploy additional payloads, steal data, and move laterally within a network undetected.
This malware primarily spreads through malvertising campaigns impersonating popular tools like PuTTY or WinSCP, and has even been used by ransomware groups such as Rhysida to compromise enterprise networks.
A Fake Microsoft Teams Installer Spreads Malware Through Ads
This new campaign combines malicious advertising and deceptive SEO tactics to rank a fake website among the top results when users search for terms like “download Teams.”

Malicious Microsoft Teams Download Site on Bing
Although neither the ads nor the domain attempt to directly mimic Microsoft's official site, they do redirect to a fake page hosted on teams-install[.]top, designed to resemble the legitimate Teams download page. What’s concerning is that clicking the download button retrieves a file named "MSTeamsSetup.exe"—the exact same name used by Microsoft’s official installer—which can easily deceive less attentive users.

Fake Microsoft Teams Site Distributes Oyster Malware Installer
Read more: ModStealer: How It Tricks Your Mac
Fraudulent Teams Installer Uses Valid Certificates and Remains Hidden in the Background
The malicious MSTeamsSetup.exe file (detected on VirusTotal) is digitally signed with valid certificates from companies like “4th State Oy” and “NRM NETWORK RISK MANAGEMENT INC.” This is done to give the file a legitimate appearance and avoid raising suspicion from both users and some security solutions.
However, once executed, the installer drops a file named CaptureService.dll (also flagged on VirusTotal) into the %APPDATA%\Roaming folder—a location commonly used by attackers to hide malicious components without triggering alerts.
To ensure the malicious code continues running, the installer creates a scheduled task named "CaptureService", which launches the DLL file every 11 minutes, even after the device is restarted. In short, it leaves an active and persistent backdoor.
This technique isn’t new. It has been seen in other fake installers for Google Chrome and Microsoft Teams, all linked to the Oyster malware—confirming that poisoned SEO and malicious ads remain highly effective tactics for compromising enterprise networks.
In similar campaigns using fake versions of tools like PuTTY, attackers exploit user trust in well-known brands and the top results in search engines. The pattern is clear: the goal is to gain initial access to systems, especially in corporate environments.
And here's the key point: IT administrators are a top target for cybercriminals, as they often hold high-privilege credentials within organizations. At TecnetOne, we recommend following these best practices to minimize the risk of infection through fake installers and malware delivered via malvertising:
-
Avoid clicking on search engine ads
-
Always download software from official or verified domains
-
Verify digital signatures and the origin of the software
Beyond tools and technical controls, people remain the most critical link in any organization’s security. Investing in awareness and ongoing training is essential to help teams recognize threats like these malvertising campaigns and respond in time. At TecnetOne, we emphasize that prevention starts with knowing what to trust—and what not to.