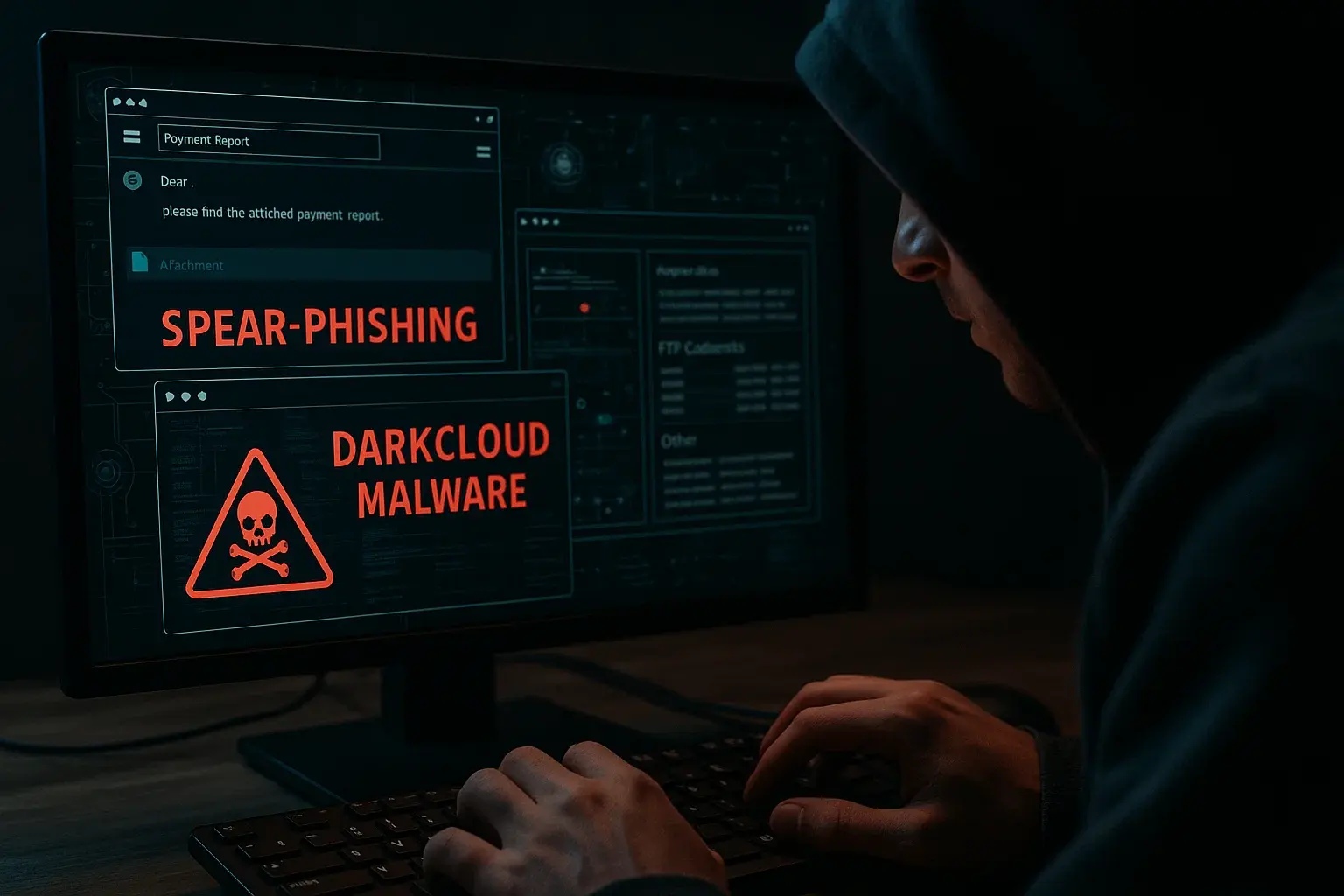
In recent weeks, cybersecurity researchers have detected a new spear phishing campaign that uses highly sophisticated social engineering tricks to spread DarkCloud—a modular malware capable of logging keystrokes, stealing FTP credentials, and extracting system information. At TecnetOne, we explain how this campaign operates and what specific actions you can take to keep your organization safer.
How the Spear Phishing Attack with Tampered Word Files Works
The attack arrives via targeted emails that appear to be legitimate notifications, such as software updates or company invoices. At first glance, these messages look completely authentic, which increases the likelihood that victims will fall for the trap.
Within the emails, attackers include a tampered Microsoft Word attachment. When opened, it triggers a multi-stage infection chain that ultimately installs the malware on the system.
Experts point out that the cybercriminals have made a notable effort in crafting convincing messages, reflecting a high level of preparation and professionalism.
The critical moment occurs when the user enables macros in the document: that's when a hidden Visual Basic (VBA) script connects to a command-and-control (C2) server, which is responsible for downloading the next malicious payload.

Phishing Lure (Source: eSentire)
The DarkCloud payload functions as an advanced loader capable of unpacking additional modules directly into memory. This allows it to evade traditional security solutions that rely on disk-based analysis and also significantly complicates any forensic investigation attempts.
To avoid detection, the malware first checks whether it is being executed in a virtual machine or a controlled analysis environment. If it detects such artifacts, it delays execution or halts it entirely.
Among its most notable capabilities is a powerful keylogger. DarkCloud injects a dynamic-link library (DLL) into common Windows processes like explorer.exe or svchost.exe. From there, it sets hooks on keyboard APIs to capture everything the victim types, including passwords and credentials for web-based FTP clients.
Once the information is collected, the malware encrypts it using a custom XOR-based algorithm and sends it to its command-and-control (C2) server. All this traffic is disguised as legitimate HTTPS communication, allowing it to blend in with normal network activity and remain undetected.

DarkCloud Website Marketed as Legitimate Software
In addition to stealing credentials, DarkCloud conducts thorough reconnaissance of the infected system. It collects metadata such as running processes, installed programs, and open network connections, and sends this information to the attackers.
With that data, the operators can fine-tune the next modules—for example, activating a plugin to exfiltrate files or another to take screenshots, all tailored to the victim’s environment.
Throughout the campaign, the attackers continually change and combine modules as needed, aiming to extract as much information as possible while leaving minimal traces to hinder any forensic investigation.
Read more: Fake Microsoft Teams Installers Distribute Oyster Malware
Infection Mechanism and Loader Dynamics
The infection begins with a lure document containing an obfuscated VBA macro. When the user enables it, the macro contacts a remote server and downloads a loader that is then injected directly into memory, rather than saved as an executable on disk. This technique makes the threat more stealthy and complicates traditional forensic analysis.
The loader decrypts the payloads using a custom routine and, once in memory, unpacks additional modules on demand. Thanks to its modular design, DarkCloud can add specific functionalities—such as file exfiltration or screen capture—as needed, without having to deploy new binaries to the system.
To remain active, the malware establishes persistence mechanisms and integrates with legitimate operating system processes, increasing both its survivability and its ability to evade detection. Moreover, the modular architecture allows operators to alternate and combine components to maximize data collection and minimize forensic traces.
In this context, traditional signature-based defenses often fall short. It is crucial to monitor for anomalous behaviors—such as unusual HTTPS sessions or processes injecting code into other executables—and to supplement with behavioral analysis, EDR, and log correlation. Rapid intelligence sharing and a coordinated incident response are essential to contain and mitigate DarkCloud’s adaptive tactics.
This is where having a Security Operations Center (SOC) becomes critical. A SOC like TecnetOne’s offers 24/7 monitoring, advanced behavior-based detection, and immediate incident response. It also conducts proactive threat hunting, forensic analysis, and leverages threat intelligence to anticipate attacks like DarkCloud.
In practice, this means drastically reducing detection time, containing the threat before it spreads, and strengthening long-term security. With a specialized SOC, organizations don’t just react—they stay one step ahead of attackers.