A new information-stealing malware known as SantaStealer has recently begun being promoted on Telegram and hacker forums. This threat is offered under the Malware-as-a-Service (MaaS) model and stands out for running directly in system memory—a technique designed to evade traditional file-based detection methods.
According to Rapid7, SantaStealer is not an entirely new project, but rather an evolution of a previous malware called BluelineStealer. The developer appears to be accelerating its rollout with the goal of launching a large-scale operation before the end of the year.
All signs point to the malware being the work of a Russian-speaking developer, who is already marketing it through a subscription-based system. Two plans are currently available: a Basic plan for $175 per month and a Premium plan for $300 per month, making it accessible even to attackers with limited technical expertise.
At TecnetOne, we continuously monitor these types of threats, analyzing how they evolve and what techniques attackers use in order to stay ahead of the risks. Being well-informed and having monitoring, detection, and response solutions in place makes all the difference when it comes to protecting critical information and ensuring business continuity.
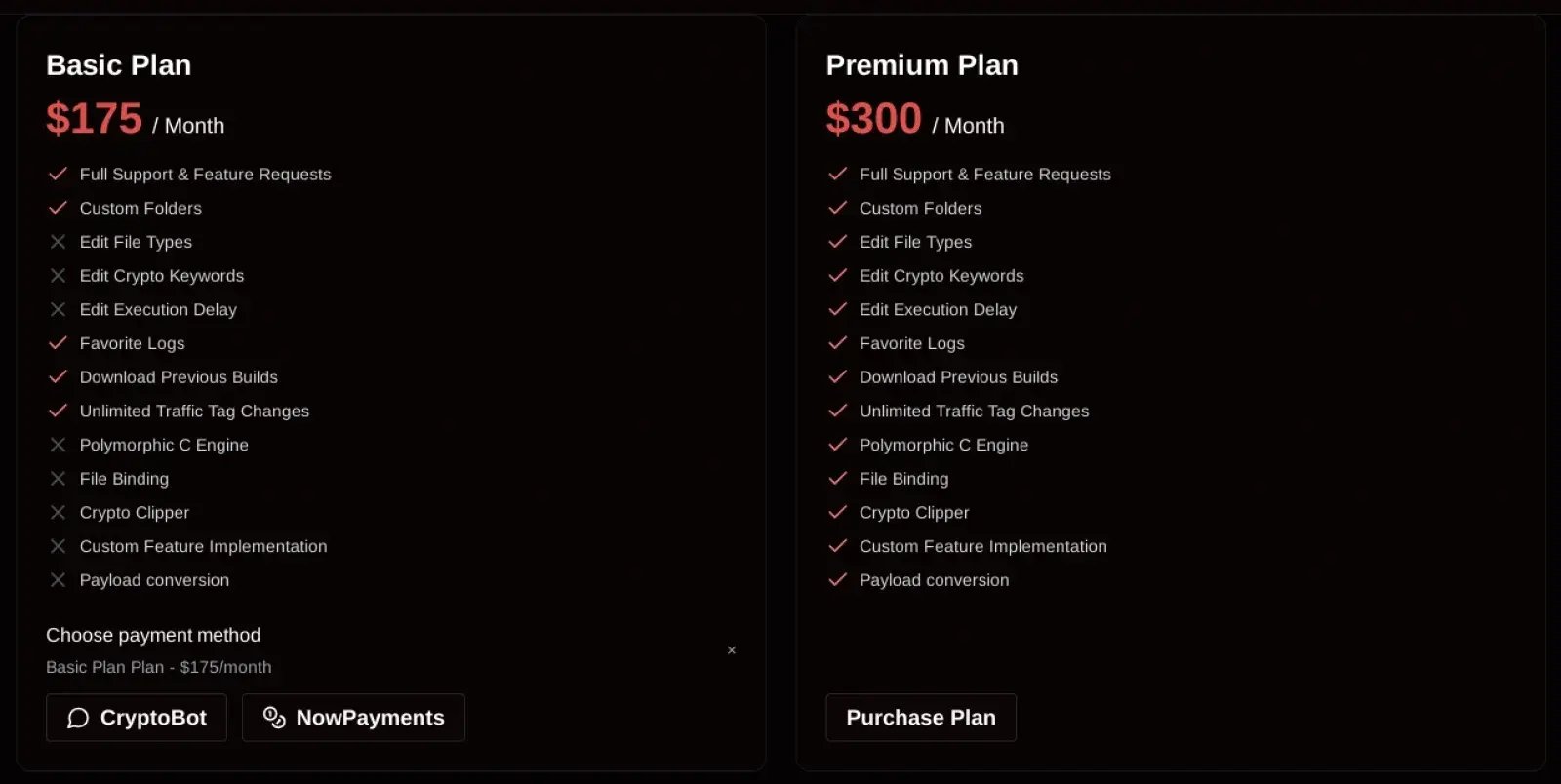
Source of the SantaStealer Announcement: Rapid7
SantaStealer Malware: How Dangerous Is It?
After analyzing various samples of SantaStealer and accessing its affiliate web panel, researchers found that the malware includes multiple mechanisms for stealing information. However, in its current state, it does not fulfill many of the functions it claims to offer, especially those related to detection evasion and security analysis.
In fact, the samples observed so far are neither undetectable nor particularly complex to analyze, indicating that the malware’s development still has significant technical weaknesses.
While it’s possible that the actor behind SantaStealer is continuing to work on more advanced anti-analysis or antivirus evasion techniques, the leak of early versions (with function names and text strings left unencrypted) reveals flaws in the project’s operation. These kinds of errors not only make analysis easier for specialists but also reduce the malware’s real effectiveness in real-world scenarios.
The control panel, for its part, features a simple and intuitive interface designed so “clients” can configure attacks according to their goals. Options range from massive data theft campaigns to lighter versions focused solely on specific information, confirming its commercial focus within the malware-as-a-service ecosystem.
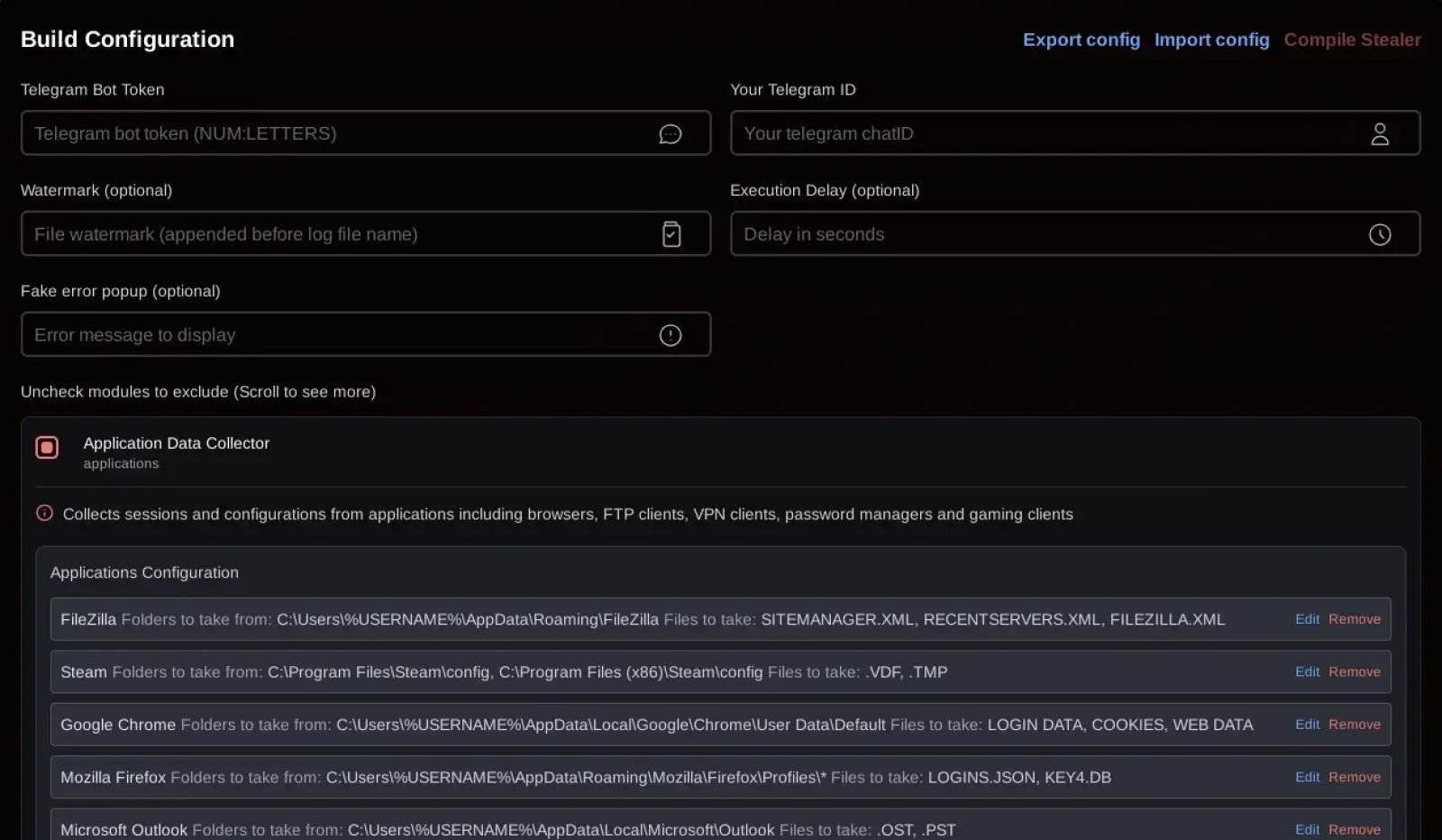
SantaStealer Configuration Operations
Read more: DroidLock: New Malware Locks Your Phone and Demands a Ransom
How Does SantaStealer Work?
SantaStealer operates through 14 distinct data collection modules, each running independently. These modules gather information directly in memory, bundle it into ZIP-compressed files, and then send it in chunks of up to 10 MB to a command-and-control (C2) server, using port 6767 for communication.
The malware targets sensitive data stored in browsers, such as passwords, cookies, browsing history, and saved credit cards. It also collects information from popular apps like Telegram, Discord, and Steam; crypto wallet extensions and applications; local documents; and can even take screenshots of the infected user's desktop.
To bypass recent security measures, SantaStealer includes an embedded executable that allows it to evade encryption protections introduced in Chrome in mid-2024—a mechanism already bypassed by several active infostealers.
SantaStealer also offers configuration options for its operators, such as the ability to exclude systems located in Commonwealth of Independent States (CIS) countries or delay execution for a set period—a common technique to avoid detection and hinder early analysis.
Since the malware is not yet fully operational or widely distributed, its primary delivery method remains unclear. However, there has been a noticeable rise in ClickFix-style attacks in recent months, where victims are tricked into copying and pasting malicious commands directly into the Windows terminal.
These are in addition to well-known techniques like phishing, pirated software downloads, torrents, malvertising, and deceptive comments on platforms like YouTube, which continue to be common malware distribution channels.
Recommendations to Protect Against SantaStealer and Other Infostealers
In the face of threats like SantaStealer, prevention and early detection remain key to minimizing the impact of a potential security incident. At TecnetOne, we recommend following essential best practices to reduce the risk of infection and data theft:
-
Be wary of unexpected links and files: Avoid opening attachments or clicking on links in emails, messages, or comments you don’t recognize—even if they look legitimate.
-
Don’t run commands without verifying their source: Attacks like ClickFix exploit users’ lack of knowledge to get them to copy and paste malicious commands. If you don’t know exactly what a command does, don’t run it.
-
Download software only from official sources: Using pirated software, cracks, or torrents remains one of the main infection vectors for malware.
-
Keep your systems and browsers up to date: Updates patch vulnerabilities that threats like SantaStealer can exploit.
-
Avoid storing sensitive information in your browser: Passwords, card details, and crypto wallet access should be protected with dedicated tools and multi-factor authentication.
-
Implement advanced monitoring and detection solutions: Having continuous visibility into system behavior allows for early detection of suspicious activity before significant damage occurs.
At TecnetOne, we offer cybersecurity solutions designed to monitor, detect, and respond to threats like SantaStealer. Through continuous monitoring services, incident response, and user awareness programs, we help businesses reduce risk, protect critical information, and ensure operational continuity.


