A hacking incident targeting the Municipal Police of Hermosillo, attributed to the group Chronus Team, has raised alarms in the cybersecurity world. The reason: the leak of a large file exposing personal, operational, and photographic information of over 1,200 municipal officers in Sonora.
The alert was triggered after a 738 MB file began circulating, reportedly containing full names, photographs, details about weapons, and internal data on the agency's operational structure. This type of information, even if outdated, poses a real risk when not properly protected.
Due to its scope and the sensitivity of the leaked data, the breach attributed to Chronus Team has become one of the most significant cyberattacks against municipal infrastructure in the past year, highlighting the urgent need for robust protection, monitoring, and incident response strategies in the public sector.
Data Breach in the Hermosillo Hack: Internal Documents, Photos, and JSON Files
The information allegedly leaked by the attackers goes far beyond isolated data points. The released file is said to include internal documents, personnel lists, photographic material, and files in JSON (JavaScript Object Notation) format—a structure commonly used to store and transfer large volumes of data in digital systems.
Within these files, sensitive categories have been identified, including operational assignments, hierarchies, days off, types of weaponry, telecommunications, fines, internal regulations, and password change logs, among others.
This level of detail not only exposes administrative information but also reveals how the agency is structured and operates, reinforcing the importance of securing data—even those considered historical or no longer in use.
Police personnel photos exposed in the leak
The breach has exposed complete files of municipal police officers, operational documents, and internal records that should be safeguarded under strict security protocols. Incidents like this not only compromise the safety of the officers but can also directly impact the tactical operations of the department by revealing information that malicious actors could exploit.
Adding to the concern, the attackers shared the leaked material alongside messages directed at authorities, claiming that their previous warnings were ignored following recent attacks—reinforcing the narrative of a lack of prevention and timely response to digital threats.
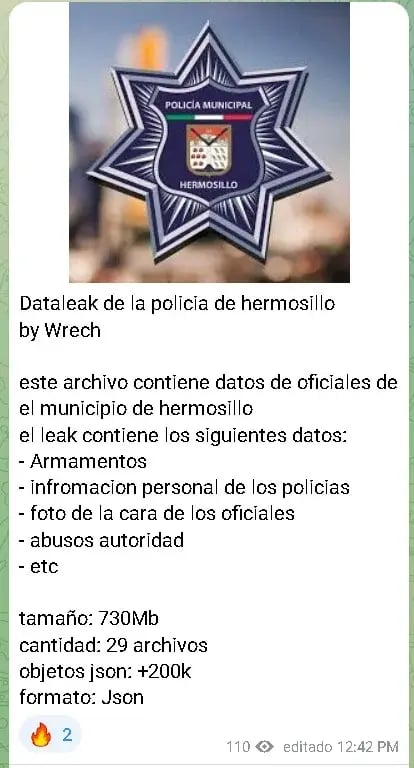
Telegram post reveals part of the leak
Read more: Mexico’s Government Network Remains Exposed
Background on Cyberattacks Against the Hermosillo City Government
The data leak is not an isolated incident. It comes just weeks after other events had already exposed weaknesses in the Hermosillo City Government's digital security. On November 6, the group Chronus Team carried out a defacement of the Budget Transparency portal, replacing the site's main content with a message directed at the authorities:
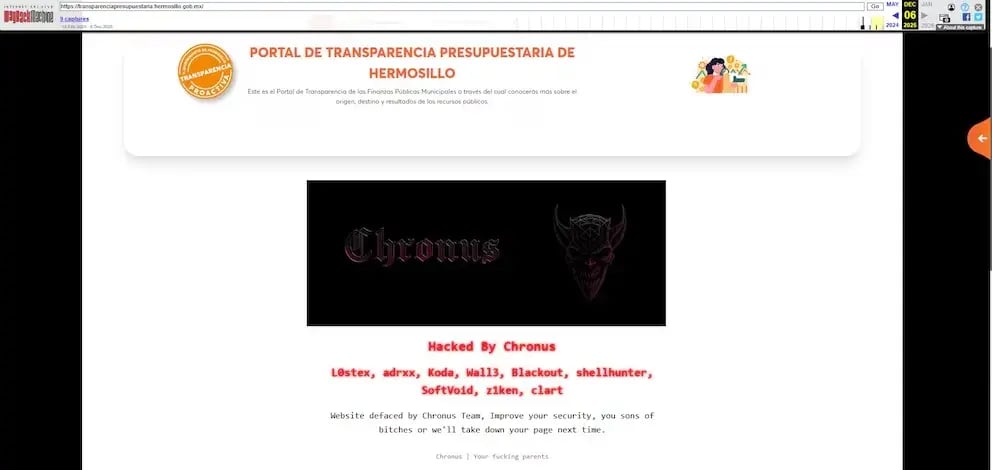
This message appeared alongside alleged signatures from members of the group, reinforcing the attribution of the attack.
The site alteration was confirmed by experts and journalists through Web Archive, a platform that preserves historical versions of websites. Screenshots verified that the official portal remained partially non-functional until November 11, temporarily affecting access to mandatory public information.
Later, on December 10, new records on the same platform revealed a second defacement of the government website, once again attributed to Chronus Team. This recurrence made clear the ongoing failures in the municipality’s cybersecurity controls and the urgent need to strengthen prevention, monitoring, and incident response strategies against digital threats.
Read more: Incident Response in Cybersecurity: What It Is and Why It Matters
Chronus Team Threatens the Government of Mexico
Chronus Team had warned that on Thursday, December 11 at 9:00 p.m., it would carry out defacements and possible intrusions on various websites of the Government of Mexico. Although the group did not specify which sites would be targeted, it made clear that its intention was to expose the vulnerabilities it believes exist within the government's digital infrastructure.

This message, shared prior to the attacks, reinforced the perception that Chronus Team was carrying out an active campaign against government entities, using hacking and defacement of official sites as a means of pressure and public exposure.
The episode once again highlighted the urgent need to strengthen cybersecurity frameworks by implementing continuous monitoring, early threat detection, and clear incident response plans.
In critical public sector environments, having a Security Operations Center (SOC) enables 24/7 system surveillance, real-time threat identification, and immediate response—reducing the impact of attacks and preventing known vulnerabilities from being exploited again.


