A new threat is making waves in the cybersecurity world: Herodotus, an Android malware that takes camouflage to a whole new level. This trojan introduces small, random delays while typing to mimic the natural rhythm of a person and thus bypass security systems that look for automated typing patterns.
Herodotus is offered as a service that anyone with malicious intent can hire (Malware as a Service), and it's already being used in real campaigns—primarily through phishing SMS messages (smishing) that trick victims into downloading a malicious app outside official app stores.
At TecnetOne, we keep you informed: we monitor new malware families and publish practical alerts to help you avoid falling into these traps.
What is Herodotus?
Herodotus malware is a new family of trojans targeting the Android operating system that, according to Threat Fabric, is distributed under a “malware-as-a-service” model aimed at financially motivated cybercriminals.
Some of its key features include:
-
It targets Android devices, including relatively recent versions (Android 9 through Android 16, according to some reports).
-
It spreads mainly via phishing SMS (also known as “smishing”), which contain a link to an installer (dropper) designed to trick the user.
-
Its installation method exploits Android's Accessibility Services to gain elevated permissions, allowing the malware to control the device interface, perform taps, typing, gestures, and more.
-
But most notably: Herodotus introduces random delays in its typing or text input actions to simulate human cadence and avoid detection by behavior-based systems that look for mechanical or overly fast patterns.
In summary: Herodotus is a mobile trojan designed to take control of Android devices, steal banking or cryptocurrency credentials, intercept two-factor authentication SMS messages, and disguise its activity as that of a legitimate user—making it especially dangerous.
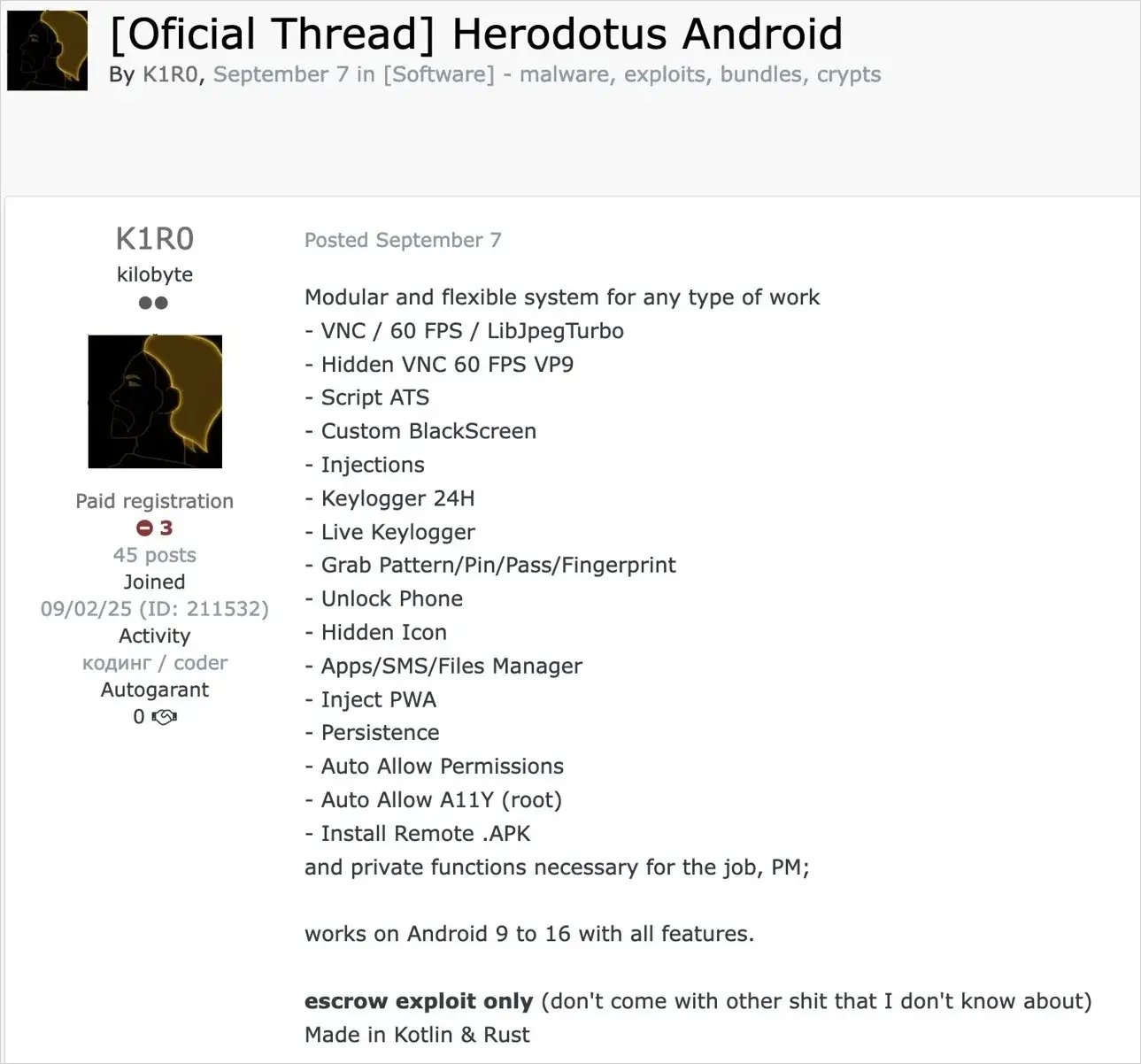
New Herodotus MaaS (Source: Threat Fabric)
How Does the Attack Work?
The Herodotus infection process follows several key stages:
1. Initial Distribution
The attack begins with a fake SMS that appears to come from a trusted entity, such as a bank or a delivery company. The message includes a link that leads to a webpage where the victim downloads a malicious app.
2. Installation and Permission Acquisition
Once the app is installed, it prompts the user to enable accessibility services, falsely claiming benefits like performance improvements or easier navigation. By doing so, the malware gains full control over the device.
3. Credential Theft
With permissions granted, Herodotus can:
-
Simulate taps or type text on the interface.
-
Display fake screens that mimic legitimate apps to steal information.
-
Read SMS messages to intercept verification codes.
-
Monitor user activity in the background.
4. Evasion of Detection
The malware’s most sophisticated feature is its ability to simulate human typing. It introduces random pauses between keystrokes—typically between 0.3 and 3 seconds—making it difficult for antivirus software or monitoring systems to detect automated behavior.
5. Data Theft and Exploitation
Once it captures credentials or banking information, attackers can perform transactions, access accounts, or send new malicious SMS messages to the victim’s contacts to continue spreading the malware.
Read more: ChatGPT Atlas: The New Vulnerability
Why Is This New Malware So Dangerous?
Herodotus poses a serious threat for several reasons:
-
Advanced Evasion: Its human-like typing technique defeats many traditional detection systems.
-
Full Control: By leveraging accessibility services, it can operate as if it were the actual user.
-
Financial Theft: It's specifically designed for banking fraud and cryptocurrency theft.
-
MaaS Model: Sold as a service, it allows any cybercriminal to use it without technical expertise.
-
Global Spread: Although initial cases were reported in Italy and Brazil, it can easily spread to other countries.
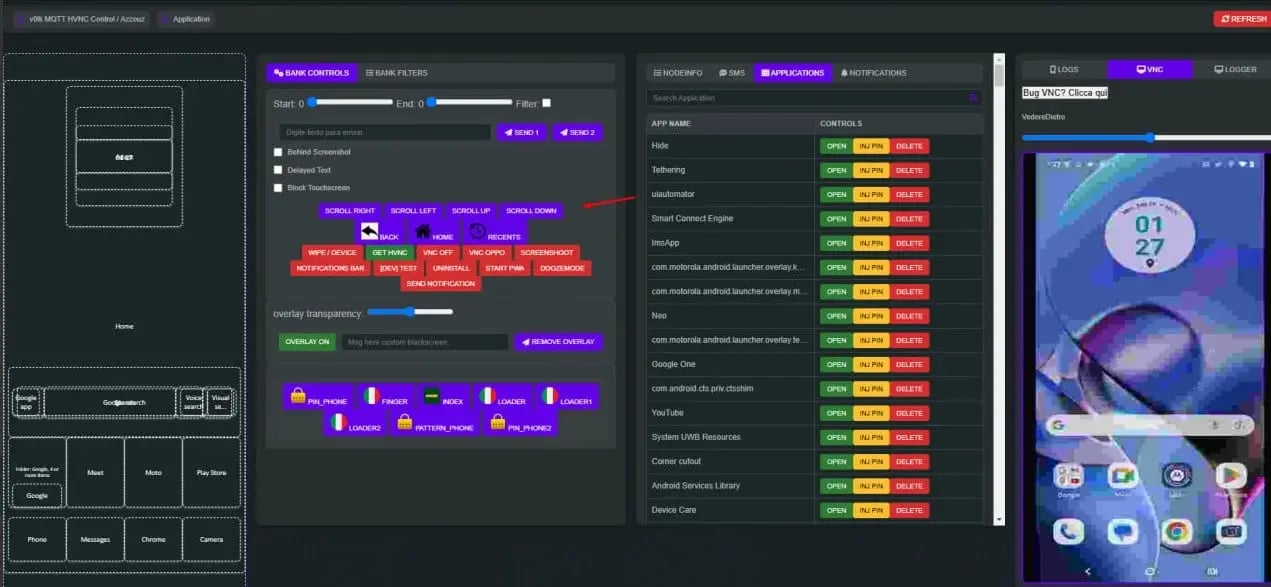
Herodotus Admin Panel (Source: Threat Fabric)
How to Detect Signs of Herodotus Infection
Although a sophisticated malware like Herodotus can hide very well, there are certain signs that may suggest an Android device is compromised:
-
Unexpected Accessibility Permission Requests: If an app asks to enable "Accessibility" without a clear reason, it’s a red flag.
-
Strange Device Behavior: For example, the screen turns black, audio is muted, or your banking app suddenly asks for unusual information.
-
Unusual Data or Battery Usage: The malware may consume background resources to communicate with command-and-control (C2) servers.
-
Unknown App Installations: If you find apps installed without your knowledge or with suspicious names.
-
Activation of Unknown Features or Unexpected Settings Changes: For instance, changing the default SMS app, sending SMS messages, or creating new contacts without your permission.
-
Alerts from Your Security Provider or Android System: Warnings like “unusual activity” or “unverified app” may appear.
If you notice any of these signs, it is highly recommended to act immediately: disconnect the device, change critical passwords, scan with a reliable mobile antivirus, revoke permissions, and consider restoring the device to factory settings.
Security Best Practices to Protect Against Herodotus
Since prevention is the best defense, at TecnetOne we know that information and preparedness are key to avoiding these threats.
That’s why we’ve prepared a set of recommendations for both individual users and organizations, which you can adapt depending on your role—whether in cybersecurity, system administration, website management, or technical support. Our goal is to help you strengthen your digital environment and keep your devices protected at all times.
For Individual Users
-
Only download apps from the official store (Google Play Store). Avoid installing APKs from unknown sources unless you're absolutely sure of their origin.
-
Enable Google Play Protect, which scans apps for malicious behavior.
-
Don’t enable accessibility services for apps that don’t clearly need them. Always verify: why does the app need this?
-
Review app permissions and revoke those that don’t make sense (e.g., accessibility, overlay screen, etc.).
-
Keep your Android OS and all apps up to date. Security patches are essential.
-
Use multi-factor authentication (MFA) that doesn’t rely solely on SMS, when possible.
-
Avoid clicking on suspicious links received via SMS, WhatsApp, or other platforms, especially from unknown numbers or messages that seem too good to be true (“you won a prize,” “update your bank info,” etc.).
-
Regularly back up your important data and consider factory resetting your device if you suspect an infection.
For Organizations / IT Administration
- Establish clear mobile security policies (MDM: Mobile Device Management) that restrict app installations from unknown sources, control critical permissions (like accessibility), and monitor device behavior.
- Use mobile security solutions with behavioral detection, not just malware signature detection, as threats like Herodotus rely on evading signatures.
- Monitor accessibility logs, screen overlay activities, external app installations, and unusual permissions on corporate devices.
- Train employees on mobile phishing, smishing, and the risks of granting permissions without verification. If your organization uses Android devices for security-sensitive services, this threat should be part of regular cybersecurity training.
- Segment networks and sensitive data to limit damage in case of device infection.
- Keep an updated inventory of allowed apps, track versions, and monitor vendor security updates.
Conclusion
The emergence of the Herodotus malware shows that mobile threats are continuing to evolve, and attackers are constantly seeking new ways to bypass security systems. Its ability to mimic human typing is a clear example of how social engineering and technical innovation are combining to make digital fraud more effective.
For users, the best defense remains prevention: avoid apps from unknown sources, review permissions, and stay informed about emerging threats.
At TecnetOne, we keep you up to date on the latest malware families, vulnerabilities, and cybersecurity trends so you can protect your devices and avoid falling victim to attacks like Herodotus. Stay informed, strengthen your digital habits, and remember: cybersecurity starts with you.

