After seven months of silence, the Gootloader malware is back in action. This threat, known for exploiting SEO poisoning to deceive users and distribute malicious files, is active once again—and more sophisticated than ever.
At TecnetOne, we closely monitor these kinds of cyber threats that endanger both businesses and individual users. That’s why, in this article, we’ll explain what Gootloader is, how its new campaign works, and what steps you can take to protect yourself before it’s too late.
What is the Gootloader Malware?
Gootloader, a malware loader written in JavaScript, spreads through compromised or attacker-controlled websites designed to appear legitimate. Thanks to SEO poisoning, these sites manage to rank among the top search results using common keywords like “non-disclosure agreement” or “legal agreement template.” When a user downloads the supposed document, they are actually triggering a silent infection on their device.
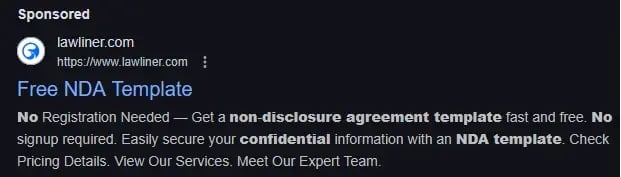
Malicious advertisement for a non-disclosure agreement template
Previously, the attackers behind Gootloader used fake forums that appeared to answer real user questions. Within those conversations, links to supposed document templates were shared—but in reality, they were malicious files.
Over time, the strategy evolved: instead of forums, the new campaigns began using websites that appeared to offer free templates for legal documents (such as contracts, agreements, or forms) to lure victims in a more convincing way.
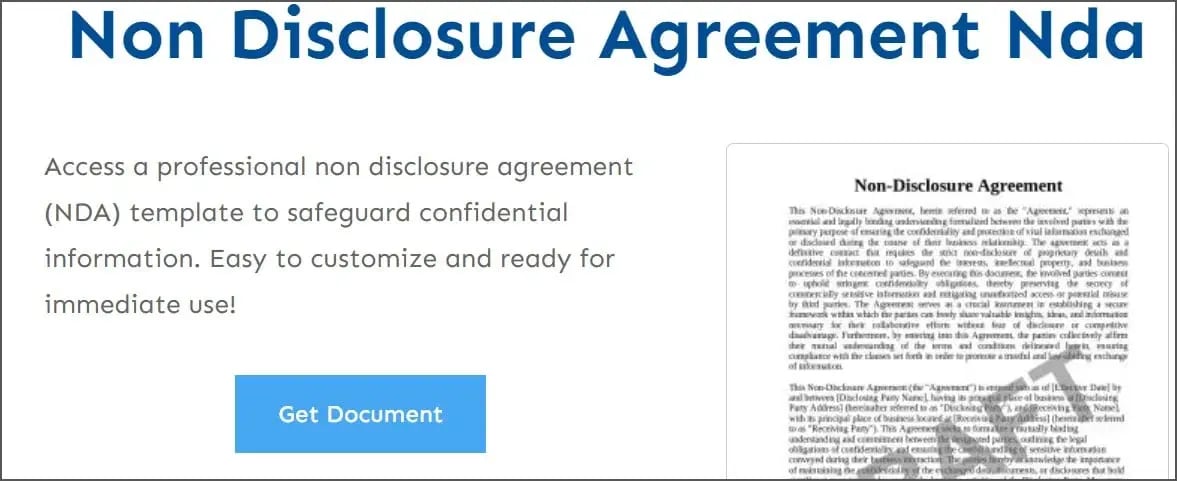
Website with fake legal agreement and document templates
When a user clicked the “Get Document” button, the site would first check if the visit was legitimate. If it passed that filter, a compressed (.zip) file would automatically download, containing what appeared to be a legal document—but was actually a malicious .js file.
For example, one of the most common filenames was mutual_non_disclosure_agreement.js, which was disguised as a harmless legal template.
Upon opening the file, Gootloader would activate and begin downloading additional malicious components onto the victim’s device. These included tools like Cobalt Strike, backdoors, and bots designed to provide initial access to corporate networks. Once inside, other cybercriminals would exploit that breach to launch more severe attacks, such as ransomware deployment or the theft of sensitive information.
Read more: How to Stop Malware on Your Company's Mobile Devices
Gootloader Malware Returns with New Tactics
After several months of silence, Gootloader has resurfaced with a new campaign that’s catching the attention of cybersecurity experts.
An independent researcher, who goes by the pseudonym “Gootloader,” has been tracking and disrupting this operation for years. Thanks to abuse reports he submitted to internet providers and hosting services, he managed to completely shut down the malware’s activity on March 31, 2025.
But the pause was temporary. In recent weeks, a new wave of Gootloader attacks has been detected, once again using SEO poisoning tactics and fake websites offering supposed legal document templates.
“In this latest campaign, we’ve identified thousands of unique keywords spread across more than 100 websites,” the researcher explained on his blog. “The goal remains the same: to trick victims into downloading a malicious ZIP file containing a JScript (.JS) script, which establishes initial access that often leads to ransomware attacks.”
The return of Gootloader highlights how cybercriminals continue to evolve their methods, exploiting user trust and infiltrating corporate networks through increasingly sophisticated social engineering tactics.
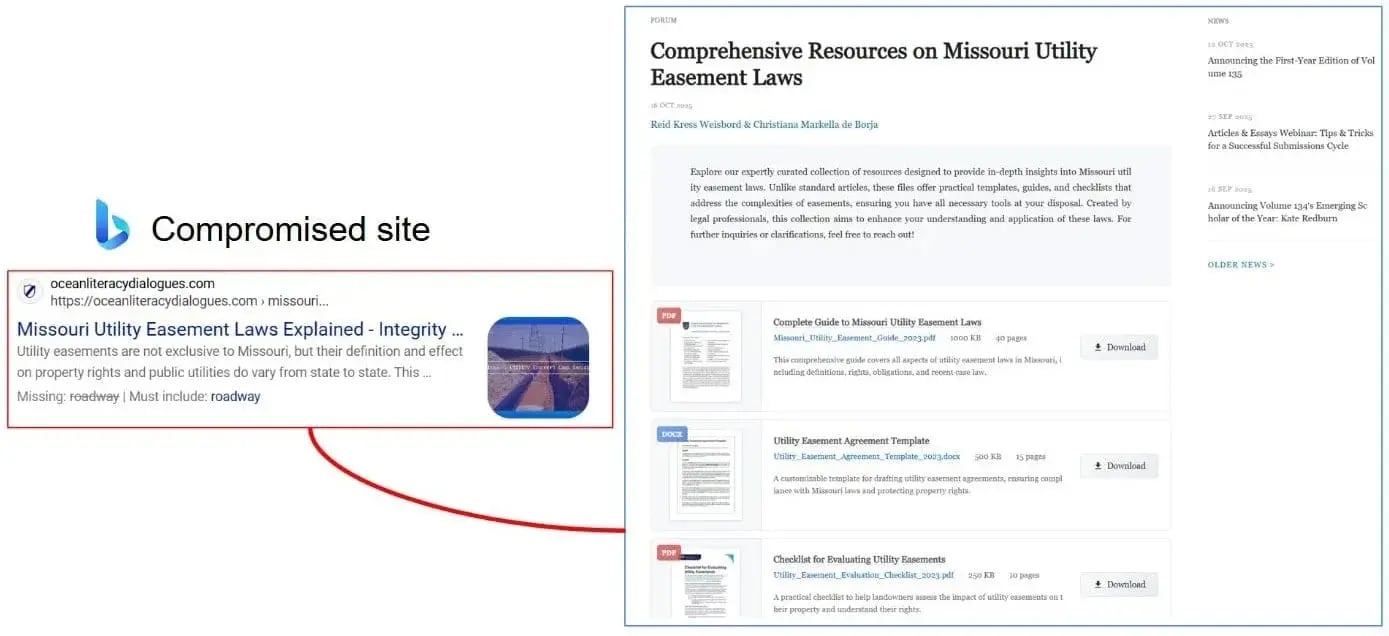
Current Attack Flow of the Gootloader Campaign (Source: Huntress Labs)
A More Elusive Variant
Researchers have pointed out that this new version of Gootloader incorporates some rather clever tricks to evade automated analysis tools and confuse security experts.
During the investigation, it was discovered that the JavaScript code injected into the malicious websites uses a highly creative technique: it hides the real file names using a custom web font. This font replaces letters with similar-looking symbols, so what appears to be meaningless text in the source code actually displays perfectly readable words on the page.
For example, in the HTML you might see a string like Oa9Z±h•, but when rendered in the browser, that combination visually transforms into the word “Florida.” In other words, the visible text doesn’t match the actual text in the code.
The trick lies in how the glyphs within the font are manipulated. Instead of using typical substitution functions or OpenType character tables, the attackers directly altered the vector shapes of each letter. So, while the character “O” may appear normal in metadata, it actually draws an “F”; the “a” draws an “l,” the “9” becomes an “o,” and even Unicode symbols like “±” end up displaying as an “i.”
This kind of manipulation makes the code look harmless to automated systems, which only see random characters, while the user sees a completely coherent page. It’s an advanced visual obfuscation technique that greatly complicates the work of researchers and delays malware detection.
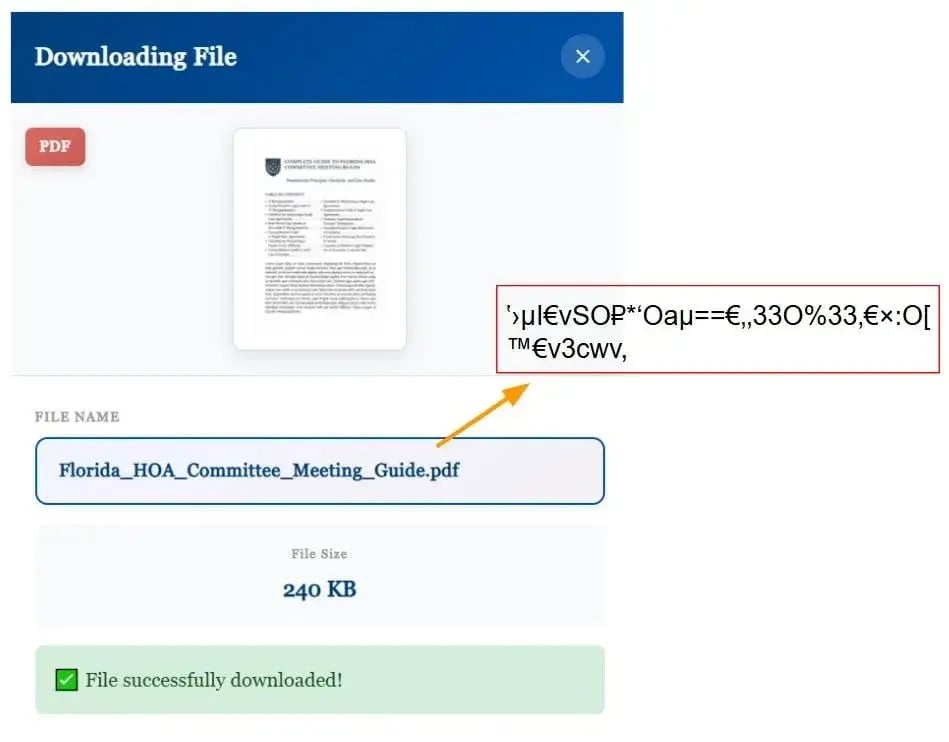
Character Mapping to Display Readable Text to Visitors
Read more: Scam Designs: How Hackers Use UX/UI to Trick You
Malformed ZIP Files: Gootloader’s New Trick
Another interesting finding is that Gootloader now uses malformed ZIP files to distribute its malicious scripts from attacker-controlled websites.
These files are designed with a dual purpose. When a user downloads and unzips them using Windows File Explorer, a malicious JavaScript file is extracted—typically named something like Review_Hearings_Manual_2025.js. This is the file that triggers the infection.
However, if the same ZIP file is analyzed with security tools or programs like VirusTotal, Python’s ZIP utilities, or 7-Zip, the extracted content is not the malicious script but rather a harmless text file named Review_Hearings_Manual_202.txt.
In other words, the file internally contains two versions of the same content but is intentionally malformed. This causes different tools to extract different results, deceiving analysis systems and making detection much more difficult.
This technique showcases the level of sophistication Gootloader has achieved: it manipulates the internal structure of the ZIP file to hide its true intent and stay under the radar of traditional antivirus tools.
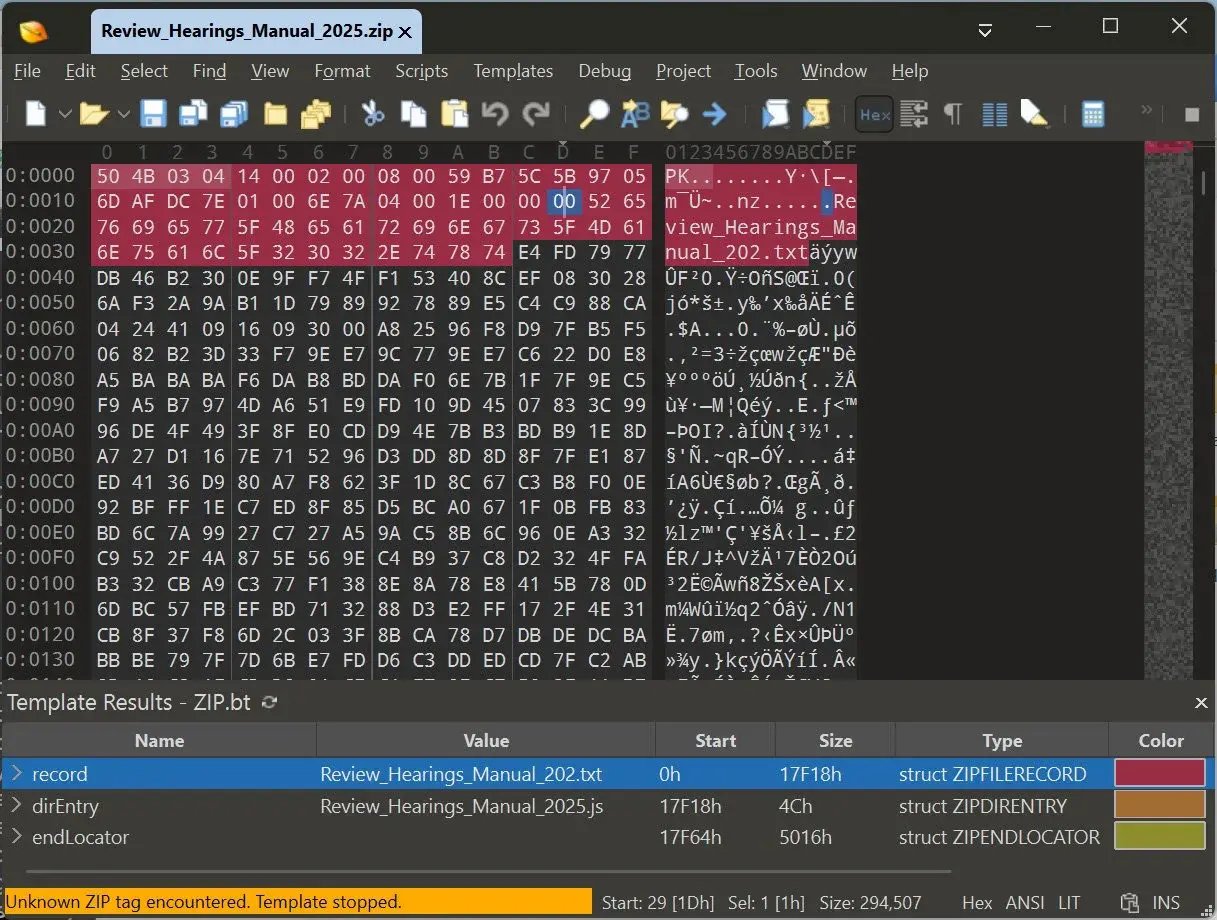
Gootloader file using a malformed archive
Gootloader Installs a Backdoor to Access Networks
It’s still unclear whether the attackers are using the same concatenation trick seen in 2024 or if they’ve developed a new technique to get Windows to extract the malicious JavaScript file. What has been confirmed is that the campaign ends by installing a backdoor known as Supper SOCKS5 on compromised devices.
This backdoor gives attackers full remote access to infected machines, allowing them to move laterally within the network and prepare more complex attacks. Supper SOCKS5 is malware used by a ransomware group known as Vanilla Tempest, which has a long history of malicious operations.
Vanilla Tempest is believed to have ties to other ransomware gangs such as BlackCat, Quantum Locker, Zeppelin, Rhysida, and even Inc—highlighting the group’s reach and expertise.
In the analyzed cases, the attackers moved with alarming speed: they performed environment reconnaissance in just 20 minutes and compromised the domain controller in under 17 hours. This kind of speed underscores the danger of Gootloader and its role as a gateway for ransomware attacks.
Now that Gootloader is active again, both corporate and individual users must be extremely cautious when searching for or downloading templates and legal documents online.
At TecnetOne, we always recommend verifying the legitimacy of websites before downloading any files and avoiding unknown or untrusted sources. If you need documents or templates for your business, make sure to obtain them from official sites or verified platforms.
Remember: sometimes a simple download can open the door to a major security breach.
That’s why it’s essential to keep your systems protected, up to date, and equipped with tools capable of detecting suspicious activity before it’s too late.
At TecnetOne, we help strengthen your company’s defenses with cybersecurity solutions designed to anticipate threats—not just react to them.


