April should be a month of organization and compliance for millions of taxpayers in Mexico, but this year, a silent threat is putting the digital security of thousands of people at risk. While many are trying to comply with their annual tax return, a malware campaign is spreading via SMS messages that impersonate the SAT with unsettling accuracy. Just one click on the fake link is enough to put your computer under the control of the attackers.
What is most alarming is that, after accessing the cloned SAT site, users are automatically redirected to fake versions of banking portals such as BBVA, HSBC, Banamex and others. This new digital fraud not only steals personal and fiscal data, but also banking credentials and access to your finances.
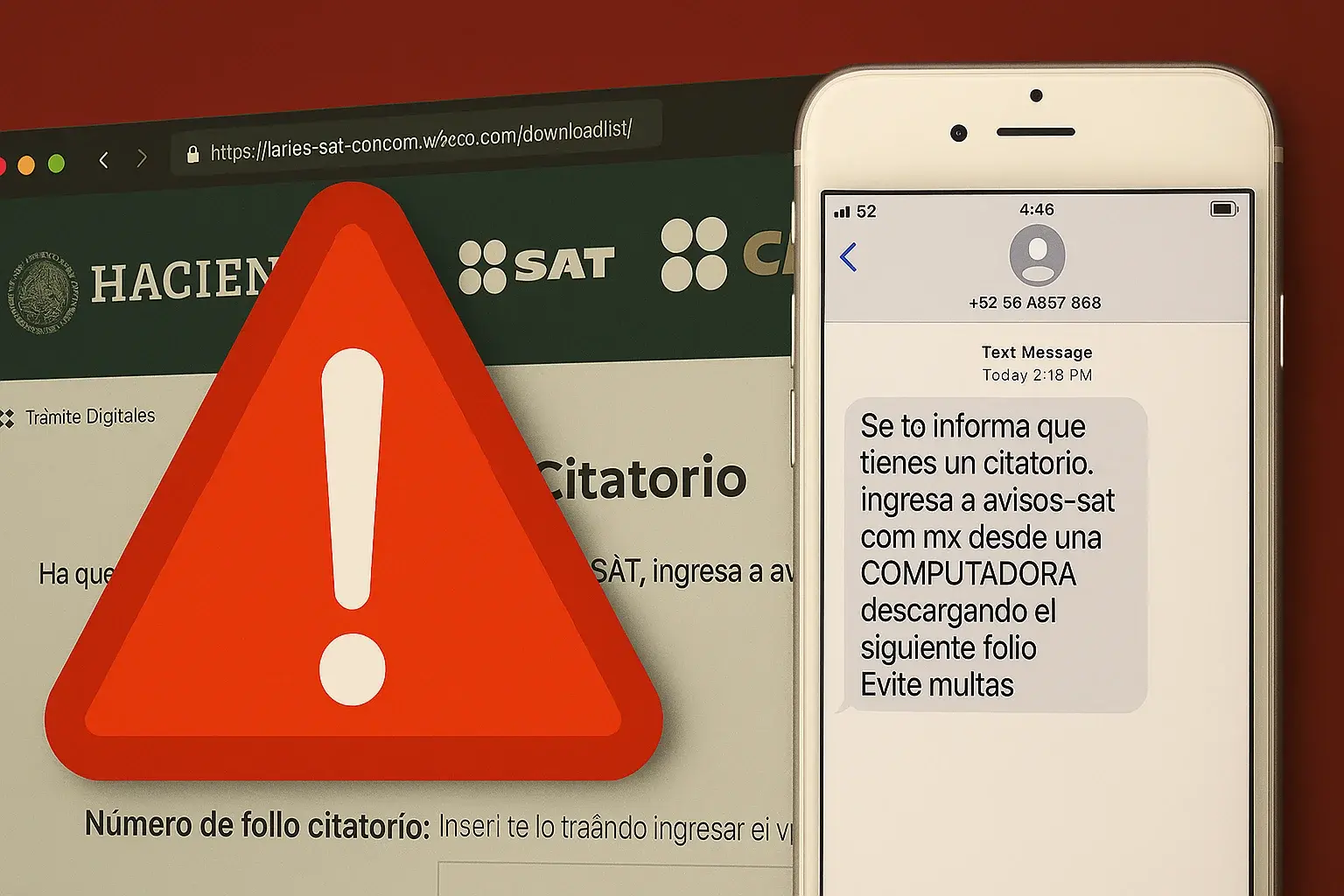
It all starts with a message from the “SAT”
It all starts with an SMS that seems to come from the SAT. The text says that you have a summons pending and invites you to enter a site called avisos-sat.com.mx. At first glance, it sounds serious and legitimate. The site looks authentic: it has the official logo, the SAT colors and even a form where you are asked for a supposed “folio number”.
What they don't tell you is that it doesn't matter what number you enter. You always get an automatic download: a .zip file with a .reg file extension, typical of Windows. And that's where the real problem starts.
What happens if you open it?
If you double-click on that file, you are basically giving the malware permission to modify how your computer behaves. According to a cybersecurity expert, that file changes the way shortcuts work on your system. Every time you click on something, a hidden command is executed in the background that downloads another malicious file... and from there, a whole chain of scripts is triggered. Meanwhile, you just see a screen that says “Windows update”, as if everything was normal. But in reality, your computer is already compromised and under the attacker's control. The worst thing is that all this happens without you even realizing it.
The real trick: The redirect without you noticing
The most dangerous thing about this virus is not just that it gets into your computer... it's what it does next. Once installed, it silently starts spying on what sites you visit. And if it detects that you try to enter pages like citas.sat.gob.mx, bbva.mx, hsbc.com.mx or banamex.com, wham! It redirects you to a fake copy of the site, which looks just like the original, but is designed to steal your passwords and bank details.
The most disturbing thing is that you don't have to do anything unusual to fall for it. Even if you type the correct address in the browser, the virus takes care of sending you to the fake site without you noticing. That's exactly what makes this scam so dangerous: it acts from behind, without you noticing that anything is wrong.

With the malware active, any visit to the SAT or your bank can take you to a fake site
Read more: U.S. Increases Tariffs and Cyber Risks to Mexican Industry
Which websites are targeted by the virus?
According to the analysis, this malware can intercept and redirect access to more than 50 legitimate websites. Yes, more than fifty. Among the most important are:
-
SAT: citas.sat.gob.mx
-
BBVA: bbva.mx, bbvanetcash.mx
-
HSBC: hsbc.com.mx, secure.hsbcnet.com
-
Banamex: bancanet.banamex.com, banamex.com
In addition to Banorte, Afirme, Inbursa, Scotiabank, Santander
Even investment platforms such as CIBanco, Masari, Ve por Más, Bansi
And payment services like Clip, STP, Invex
The virus contains this list within its own code, which demonstrates how well-planned the attack is. Cybersecurity experts have managed to extract this information and share it publicly.

The Malware: Yes, They Can Take Over Your Entire Computer
Once the malicious file is downloaded, it installs a program called a RAT (Remote Access Tool) — in this specific case, it's RuRAT. And what does it do? Basically, it gives the attackers full control of your computer. Literally, they can:
-
See everything you do on your screen.
-
Steal your files or passwords.
-
Install more viruses without you noticing.
-
Even access your banking sessions in real time.
The worst part? All of this is coordinated from servers located abroad, mainly through Russian domains and platforms like DigitalOcean, which makes it extremely difficult to track down those responsible.
Read more: What is Phishing? Protect Yourself from Digital Deception
There Are Already Confirmed Victims
This isn't theory or speculation. At least 41 infected computers have already been detected, according to digital security intelligence reports. The findings are active and have been shared on platforms like MalwareBazaar, which track real-world threats.
The files used to infiltrate systems have deceptive names, such as:
-
fisherprice.msi(yes, like the toy brand) -
LinLibrary.dll(a library that spies on your browsing) -
Citatorio_folio_XXXXXX.reg(the infamous file that starts it all)
What’s the Goal Behind All This?
The intention is clear: to take advantage of the fact that half the country is logging into SAT and their bank accounts, in order to steal credentials, access accounts, and commit financial fraud.
And since the malware modifies your browser’s behavior, you no longer need to fall for a phishing link to be affected. You type in the correct URL, think everything’s fine... but the system redirects you to a cloned page that looks identical. And that’s where your data is stolen.