The Wazuh Cyber Threat Intelligence (CTI) service is like having an up-to-date radar that alerts you when there are cyber threats or vulnerabilities out there. It is a public platform that collects, analyzes, and shares useful information about new risks that may affect the security of your systems.
This first version of the service focuses primarily on vulnerability intelligence. What does that mean? It keeps you informed about known security flaws (the famous CVEs), tells you how serious they are, whether they are being actively exploited, and what you can do to protect yourself. To ensure that the information is reliable and relevant, Wazuh collects this data from trusted sources (such as operating system vendors and recognized databases) and cleans and organizes it before presenting it to you.
The result? You (or your company) can reduce the chances of being attacked, plug holes before someone exploits them, and avoid headaches such as data breaches.
And it doesn't stop there: with version 5.0 of Wazuh, the CTI service is going to become even more powerful. It will include other types of threat intelligence, such as indicators of compromise (IOCs), including suspicious IPs, malicious file hashes, and dangerous URLs. In addition, threat detection rules will also come directly from this platform, making things much easier.
Where does Wazuh CTI get its vulnerability information?
To provide reliable and up-to-date data, the Wazuh CTI platform draws on a number of well-known and trusted sources. On the one hand, it takes information directly from operating system vendors such as AlmaLinux, Amazon Linux, ArchLinux, Ubuntu, Debian, Fedora, Oracle Linux, Red Hat (RHEL), Rocky Linux, and SUSE, among others. On the other hand, it also consults recognized security databases such as:
-
Microsoft Security Updates (MSU)
-
The National Vulnerability Database (NVD)
-
Open Source Vulnerabilities (OSV)
-
And even reports from CISA (the US Cybersecurity and Infrastructure Security Agency).
This ensures that they cover a fairly comprehensive landscape.
How does Wazuh CTI handle all this information?
Now, it's not just a matter of copying and pasting data. Wazuh has a very careful workflow to process all this information accurately and orderly. Here's how they do it:
1. Collection and standardization
Since each provider has its own way of publishing data, the first thing Wazuh does is collect everything and put it through a “normalization” process. Basically, it converts all the information into a standard format (CVE JSON 5.0) to make it easier to manage and compare.
2. Thorough validation
Next, the team investigates which specific systems and versions are actually affected by each vulnerability. No assumptions or copying without verification. This stage is key to ensuring that the data is accurate and reliable.
3. Adjustments and enrichment
Then comes a kind of cleaning and improvement: formatting errors are corrected, missing information is filled in, and everything is ensured to be well presented. This makes the final result much more useful and understandable.
Once they go through this entire process, the data is ready to be shared. It is uploaded to a central repository and then published via Wazuh's CTI API, ready for users to consult and use to improve their security.
Read more: Wazuh 4.12.0: Everything You Need to Know About the New Version
How do I access Wazuh CTI?
Accessing Wazuh CTI is super easy. This tool feeds both the public threat intelligence website and the vulnerability detection feature within Wazuh's unified XDR and SIEM platform. So you can check it out wherever you feel most comfortable: the Wazuh CTI website or directly from your Wazuh dashboard, in the section called “Vulnerability Detection.”
From the website
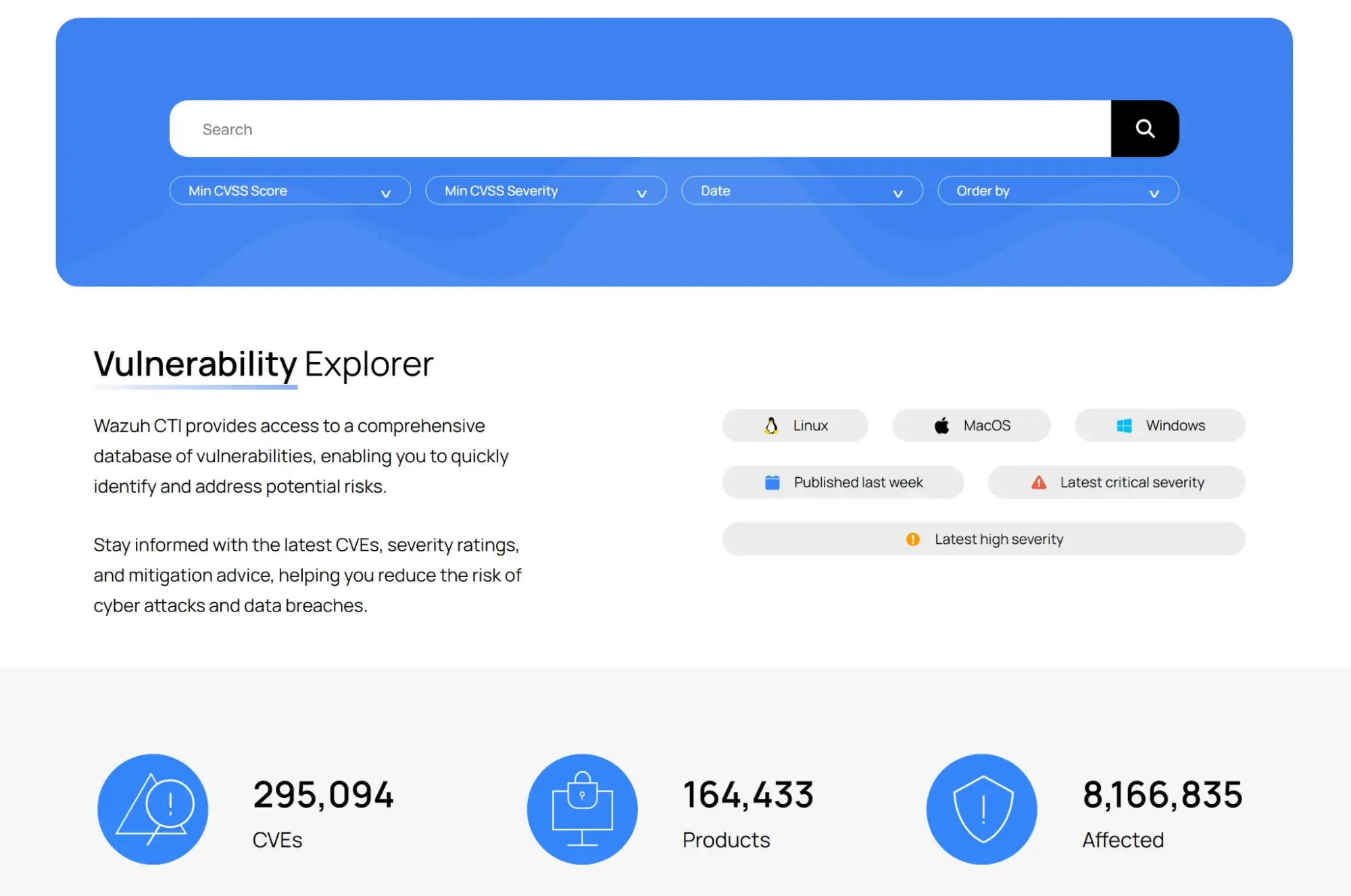
The Wazuh CTI website is open, anyone can use it, and (good news!) you don't need to have Wazuh installed to consult it. It's very easy to use and comes with a comprehensive search tool, ideal for filtering vulnerabilities by:
-
CVE ID
-
Affected application or system
-
Severity level (CVSS)
-
Publication date
- And more options to customize your search
It's perfect if you want to do quick searches, investigate specific vulnerabilities, or simply stay up to date with what's happening in the world of cybersecurity.

You can also explore CVE data by source, review vulnerability trends by year, and see which ones are most searched for by other users. It's a super useful way to stay on top of what's happening in the world of cybersecurity and find out which vulnerabilities are generating the most buzz.

From the Wazuh dashboard
Starting with version 4.12 of Wazuh, you can now access Wazuh CTI directly from the vulnerability alerts on the same dashboard. How? It's super easy: just go to Vulnerability Detection > Inventory and click on the little button for any unresolved issue. This will take you to the Wazuh CTI page, where you can see all the details related to that vulnerability.

For example, if you click on CVE-2025-0411, it takes you directly to information about a problem in the 7-Zip package, which has a flaw that allows attackers to bypass the Mark-of-the-Web (MotW) security system.
Once you are on the CTI site, you will find everything you need: a description of the vulnerability, which systems and versions are affected, how serious it is, and even links to read more about it. Below you can see how that specific vulnerability appears on the Wazuh CTI site.

Conclusion
Wazuh CTI is like your personal intelligence center against cyber threats. It collects, analyzes, and shares useful information about vulnerabilities and risks that could affect you. For now, it is very focused on everything related to known vulnerabilities, but the idea is that future updates will expand to cover more types of threats.
In addition, it will also update the Wazuh rule set, which means that threat detection will become increasingly accurate and faster. In short: Wazuh CTI is a tool that continues to improve and can become a key part of your digital security strategy.