A new phishing kit called SpiderMan is targeting customers of various European banks as well as users of cryptocurrency services, using nearly identical replicas of legitimate websites to trick victims without them noticing.
What’s particularly concerning is that these campaigns don’t just steal usernames and passwords. They can also capture verification codes (2FA) and even card details, enabling much faster and more damaging fraud.
At TecnetOne, we closely monitor these kinds of threats because they reflect today’s reality: phishing is no longer obvious or improvised; now it looks professional, moves quickly, and relies on tools designed to steal information in real time.
According to recent reports, this kit is already targeting financial institutions in five countries, including brands like Deutsche Bank, ING, Comdirect, Blau, O2, CaixaBank, Volksbank, and Commerzbank.
How Does SpiderMan Phishing Work?
The latest analyses show that this tool isn’t limited to traditional banking: it can also generate fake pages for fintech and payment platforms like Klarna (Sweden) and PayPal, replicating their login experience so the deception goes unnoticed.
And watch out for the crypto side: beyond stealing login credentials, it can also go after the most valuable data—seed phrases—targeting wallets like Ledger, MetaMask, and Exodus.
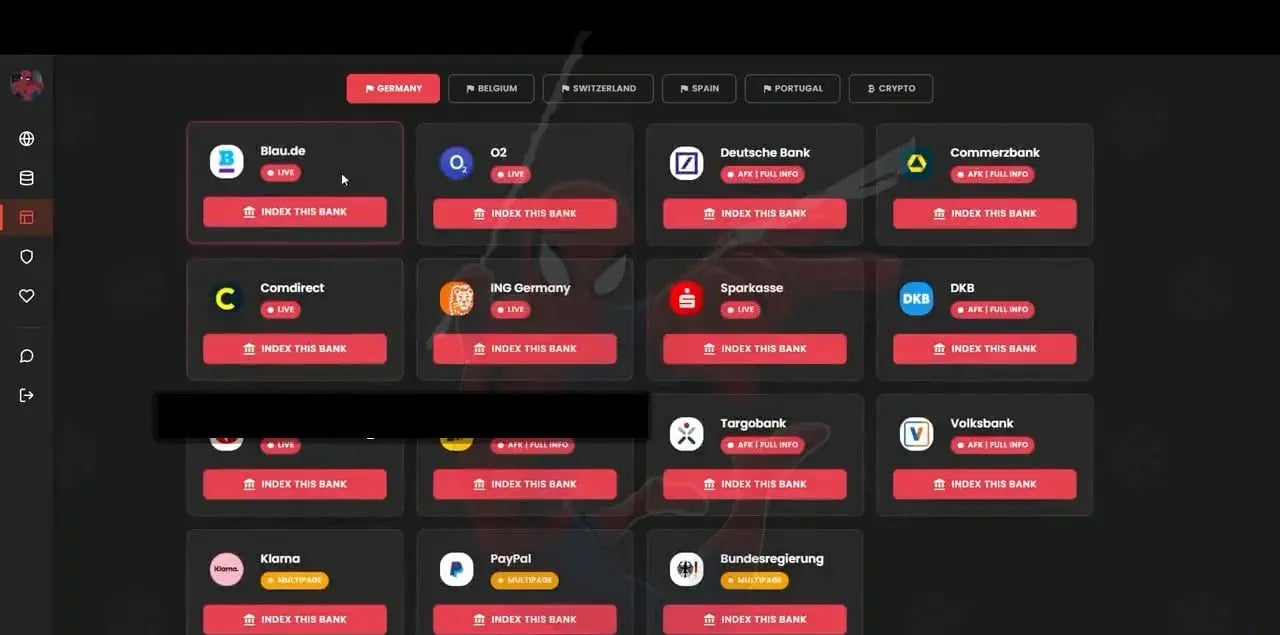
Some of the targeted platforms (Source: Varonis)
Because this kit is modular, attackers can keep adding new banks, platforms, and even authentication methods almost like “plugins.” And as digital banking in Europe updates its processes, it’s highly likely this phishing tool will adapt at the same pace.
What’s more, it already appears to have significant traction in the criminal world: researchers have identified a Signal group with around 750 members, suggesting that the kit is being shared, tested, and continuously improved.
What’s most alarming is the level of “operation” it offers. From a control panel, attackers can view the victim’s session in real time, capture credentials, export data with a single click, intercept PhotoTAN/OTP codes on the spot, and even collect credit card information. In other words, this is not basic phishing—it’s a platform designed to steal data quickly and efficiently.
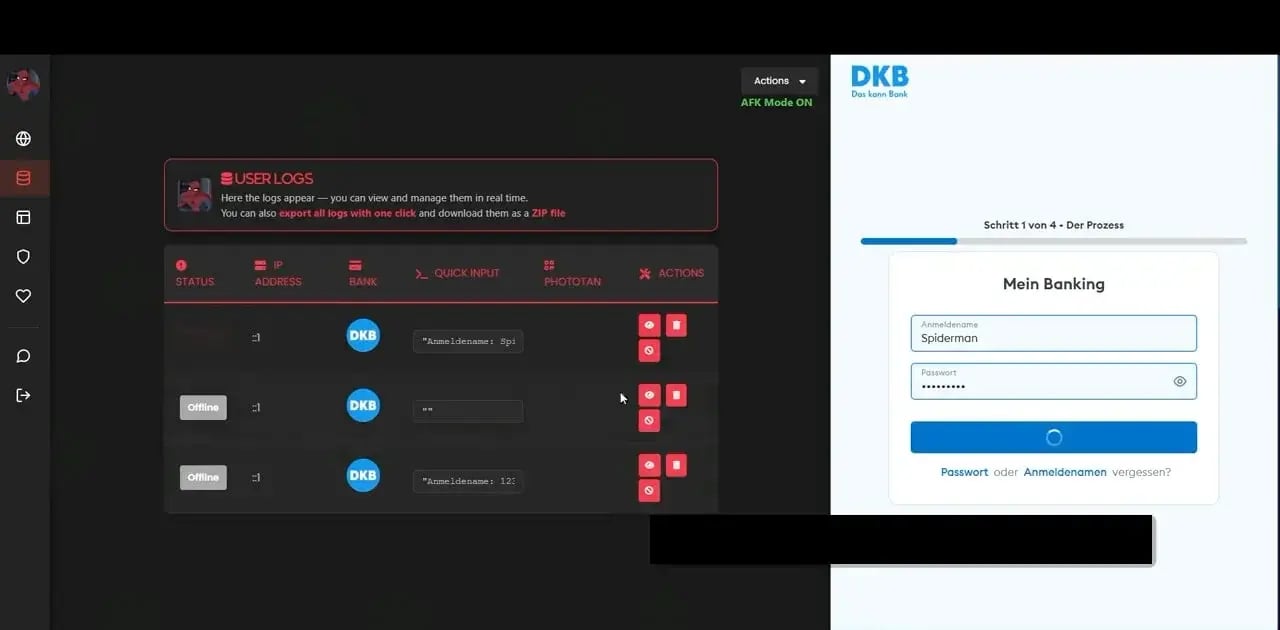
Real-Time Interaction Through the Control Panel (Source: Varonis)
Read more: How to Combat AI-Powered Social Engineering Attacks
PhotoTAN Under Attack: How SpiderMan Phishing Exploits It and How to Protect Yourself
PhotoTAN is a verification system (OTP) commonly used by European banks. Here’s how it works: during login or when approving a transaction, the bank displays a mosaic-style image in color. You scan it with the bank’s app, which then generates a unique code to proceed.
The app “translates” the mosaic and returns a one-time password (OTP) tied to that specific operation, which you then have to enter again on the bank’s website to complete the process.
While capturing PhotoTAN codes isn’t exactly new in the phishing world, today it’s considered almost essential for any phishing kit aiming to effectively target European banks.
In SpiderMan’s case, attackers can tweak their campaigns directly from a control panel: selecting specific countries, using whitelists (e.g., certain internet providers), filtering by device type (mobile or desktop), and even redirecting users they’re not interested in—to avoid raising suspicion or wasting attempts.
If someone falls for it, the stolen data can lead to full account takeovers, SIM swapping (to intercept messages), credit card fraud, and identity theft.
That’s why the golden rule still applies: never enter your credentials through links, and always double-check that you’re on the official domain before entering your username and password. Also, watch out for a growing trick: fake “windows within the browser” designed to make it look like the URL is legitimate when it isn’t.
And here’s a key tip from TecnetOne: if you receive an SMS or a PhotoTAN notification that you didn’t request (without trying to log in or make a payment), treat it as a serious fraud warning and report it to your bank immediately.

