A new cyber threat is beginning to take shape: ShinySp1d3r, a Ransomware-as-a-Service (RaaS) platform currently in development, but already showing signs of the potential scope of its future extortion operations.
Behind this emerging RaaS are actors linked to the cybercrime groups ShinyHunters and Scattered Spider, both known for their involvement in high-profile attacks and large-scale data theft. Until now, these groups have typically relied on encryptors from other ransomware gangs such as ALPHV/BlackCat, Qilin, RansomHub, and DragonForce. However, all indications suggest they are now creating their own ransomware infrastructure, which will allow them to launch attacks directly or through affiliates.
The existence of ShinySp1d3r came to light through a Telegram channel, where a collective calling itself "Scattered Lapsus$ Hunters" (a blend of the names Scattered Spider, Lapsus$, and ShinyHunters) began publicly extorting data breach victims, including Salesforce and Jaguar Land Rover (JLR).
At TecnetOne, we are analyzing the behavior of this new threat to detect trends, identify risks, and offer concrete solutions to improve cybersecurity day by day.
The ShinySp1d3r Encryptor: Built from Scratch by ShinyHunters
A sample of the ShinySp1d3r ransomware was recently uploaded to VirusTotal, and since then, new variants have surfaced, allowing researchers to further analyze how this new encryptor works.
Although in some screenshots it appears written as Sh1nySp1d3r, it has been confirmed that the official name of the project is ShinySp1d3r, and that version is expected to remain in future updates of the malware.
Unlike other groups that reuse leaked code from projects like LockBit or Babuk, ShinyHunters is developing this ransomware from scratch. This gives them greater control over the encryptor’s capabilities and reinforces the notion that they are aiming to build a completely independent and more sophisticated operation.
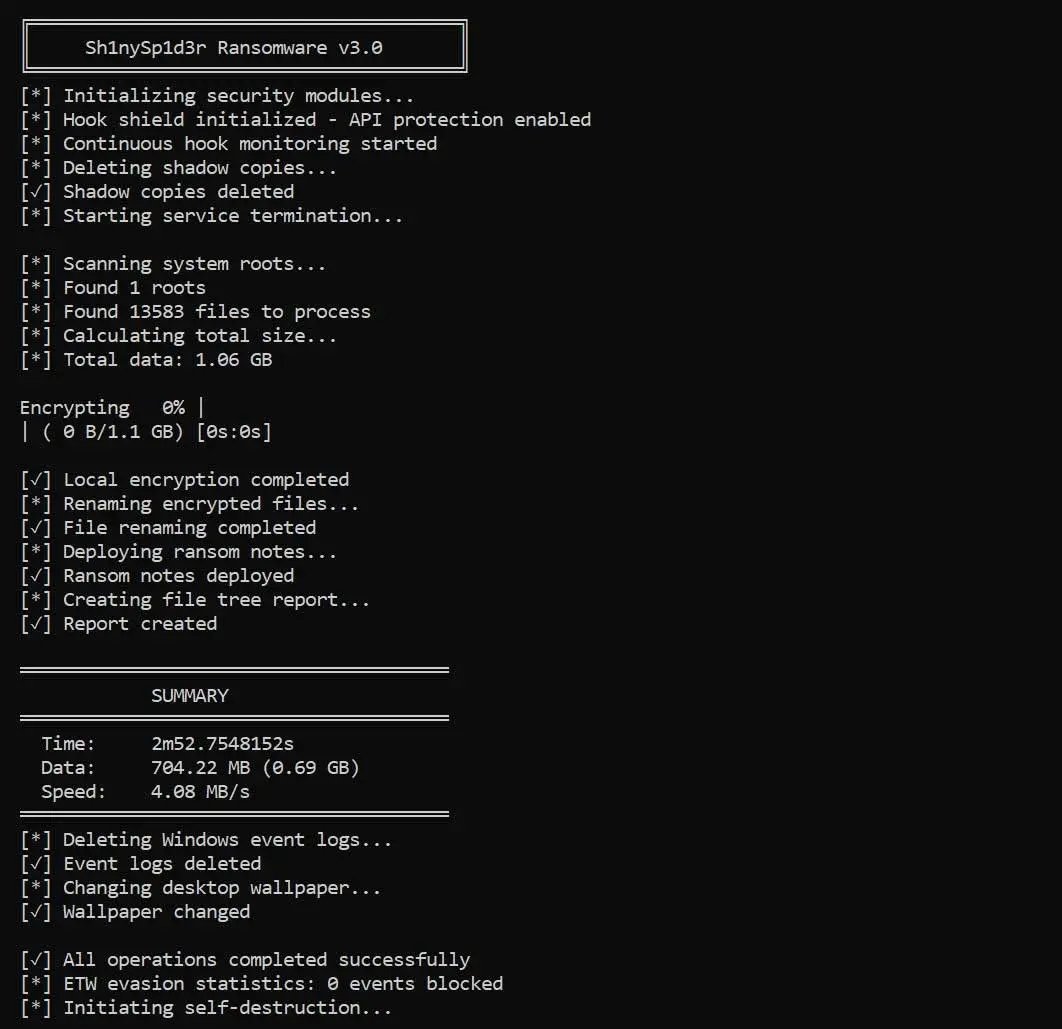
ShinySp1d3r Ransomware (Source: BleepingComputer)
Read more: Ransomware Attack Indicators: How to Identify Them?
What Makes the ShinySp1d3r Encryptor So Special?
The Windows encryptor developed by ShinySp1d3r is far from ordinary. While it includes many features seen in other ransomware, it also incorporates some rather unusual and advanced capabilities that have caught the attention of analysts.
Here are some of the most notable functionalities identified so far:
-
Hides its tracks in the system by intercepting the EtwEventWrite function, which prevents certain events from being logged in the Windows Event Viewer.
-
Terminates processes that prevent file encryption, even if the files are in use. It identifies the processes that have a file open and shuts them down. It also includes a function called forceKillUsingRestartManager, which leverages the Restart Manager API—though this function has not yet been active in the analyzed samples.
-
Overwrites free disk space by writing temporary files with random data (e.g., wipe-[random].tmp). This destroys deleted files, making recovery nearly impossible.
-
Kills a specific list of processes and services, likely to prevent interference during the attack.
-
Calculates the optimal amount of data to read based on available memory to maximize encryption efficiency.
-
Can spread to other devices on the local network using various methods such as:
-
deployViaSCM: creates a service that runs the ransomware.
-
deployViaWMI: launches it remotely using WMI.
-
attemptGPODeployment: generates a startup script via GPO to execute the malware.
-
-
Includes anti-analysis techniques, such as overwriting memory buffers, to hinder reverse engineering and forensic analysis.
-
Deletes Windows backup copies (shadow copies), a classic tactic to prevent recovery of encrypted files.
-
Scans the network for open shared resources and encrypts them if access is granted.
-
Uses a sophisticated encryption scheme, fragmenting files into parts with different sizes and offsets. It’s not entirely clear why, or whether this information is stored in an encrypted header to assist with recovery after ransom payment.
-
Encrypts files with ChaCha20, a fast and secure encryption method, and protects the key with RSA-2048. Additionally, each encrypted file receives a unique extension generated through a mathematical formula, giving each affected file an individual "signature."
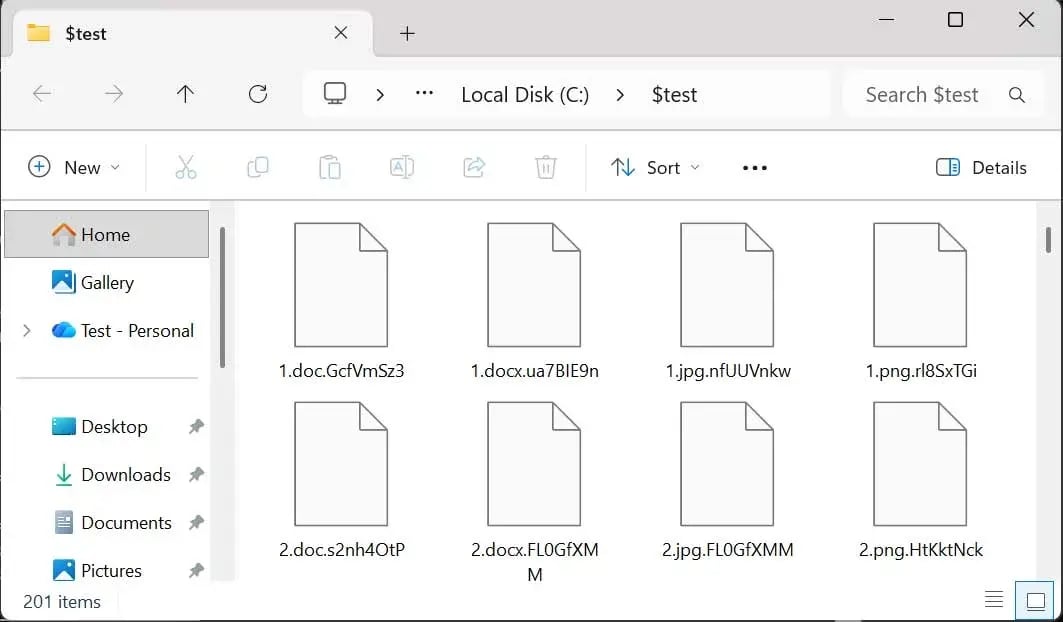
Folder Encrypted by ShinySp1d3r Ransomware
How ShinySp1d3r's Headers and Ransom Notes Work
When ShinySp1d3r encrypts a file, it adds a special header that starts with SPDR and ends with ENDS. This header contains key information about the encrypted file, such as the original filename, an encrypted private key, and other technical metadata required for the decryption process (assuming the ransom is paid—though this practice is strongly discouraged).
Additionally, in every folder where files have been encrypted, the ransomware drops a ransom note. The note briefly explains what happened, provides instructions for negotiating the ransom, and includes a TOX address—the attackers’ chosen communication channel for maintaining anonymous, encrypted contact with the victim.
The ransom note left by ShinySp1d3r includes a link to a supposed data leak site on the Tor network. However, this is currently a non-functional .onion URL, suggesting that the site is still under development or awaiting activation.
The message begins with a serious, direct tone:
“This communication has been issued on behalf of the ShinySp1d3r group. It is intended solely for internal incident response personnel, technical leadership, or designated external advisors.”
The note goes on to state that a critical incident has occurred in the victim’s infrastructure, indicating that multiple digital assets have been encrypted and that some data has been backed up—meaning it was stolen prior to encryption.
It also clarifies that the attackers' goal is not to disrupt operations, but to offer an "opportunity" to resolve the incident confidentially, quickly, and (in their words) definitively. This reflects a double extortion strategy, in which not only is access to files blocked, but there is also the threat of data leakage if the ransom is not paid.
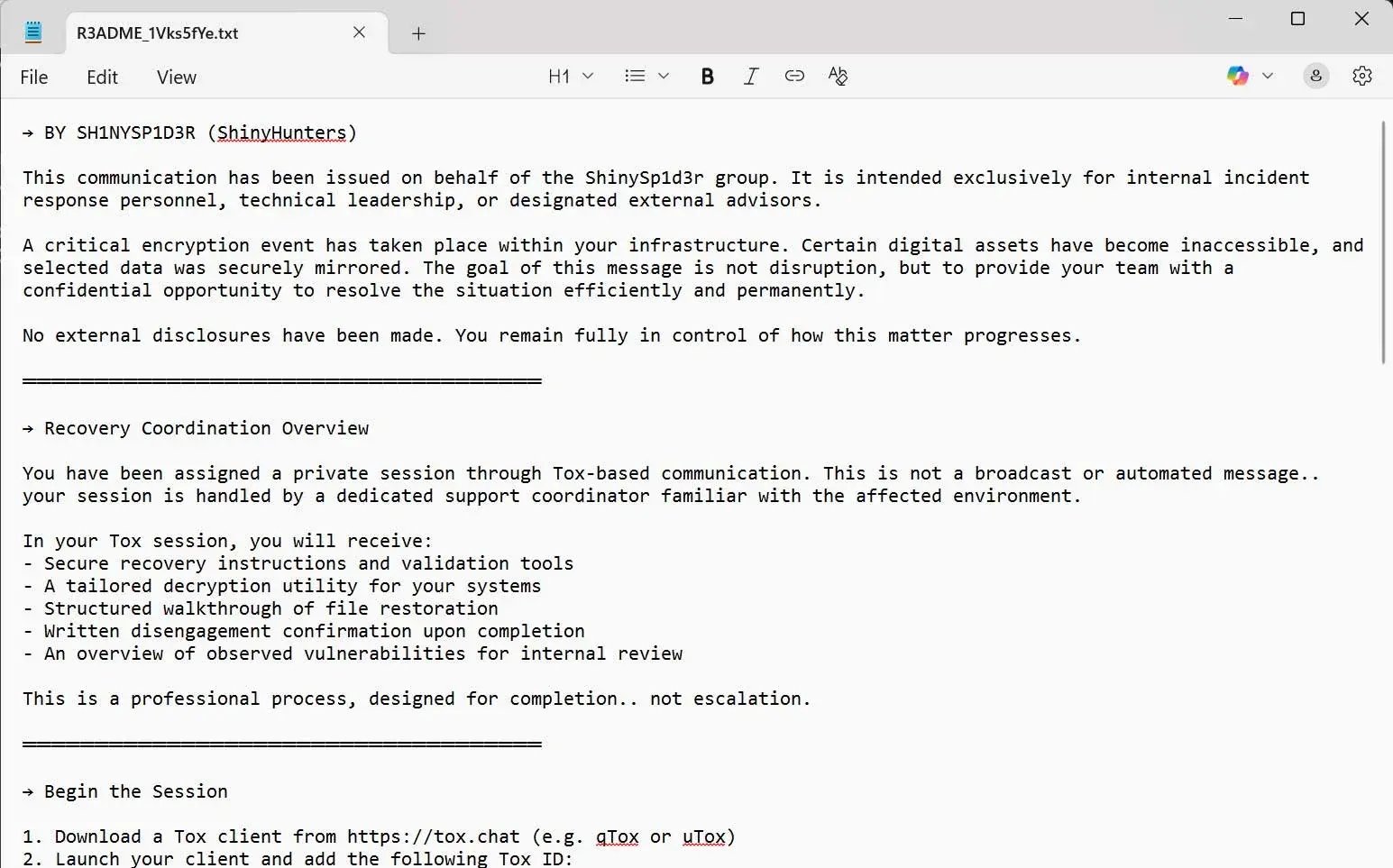
ShinySp1d3r Ransom Note
The ShinySp1d3r ransom note leaves little room for negotiation: victims are given a three-day deadline to initiate contact. If they fail to do so, the attackers threaten to publicly disclose the incident on their data leak site on the Tor network.
In addition to dropping the usual ransom notes in each affected folder, the ransomware also changes the Windows desktop wallpaper of the compromised system. The new background warns the victim about the attack and urges them to read the ransom note to understand what steps to take.
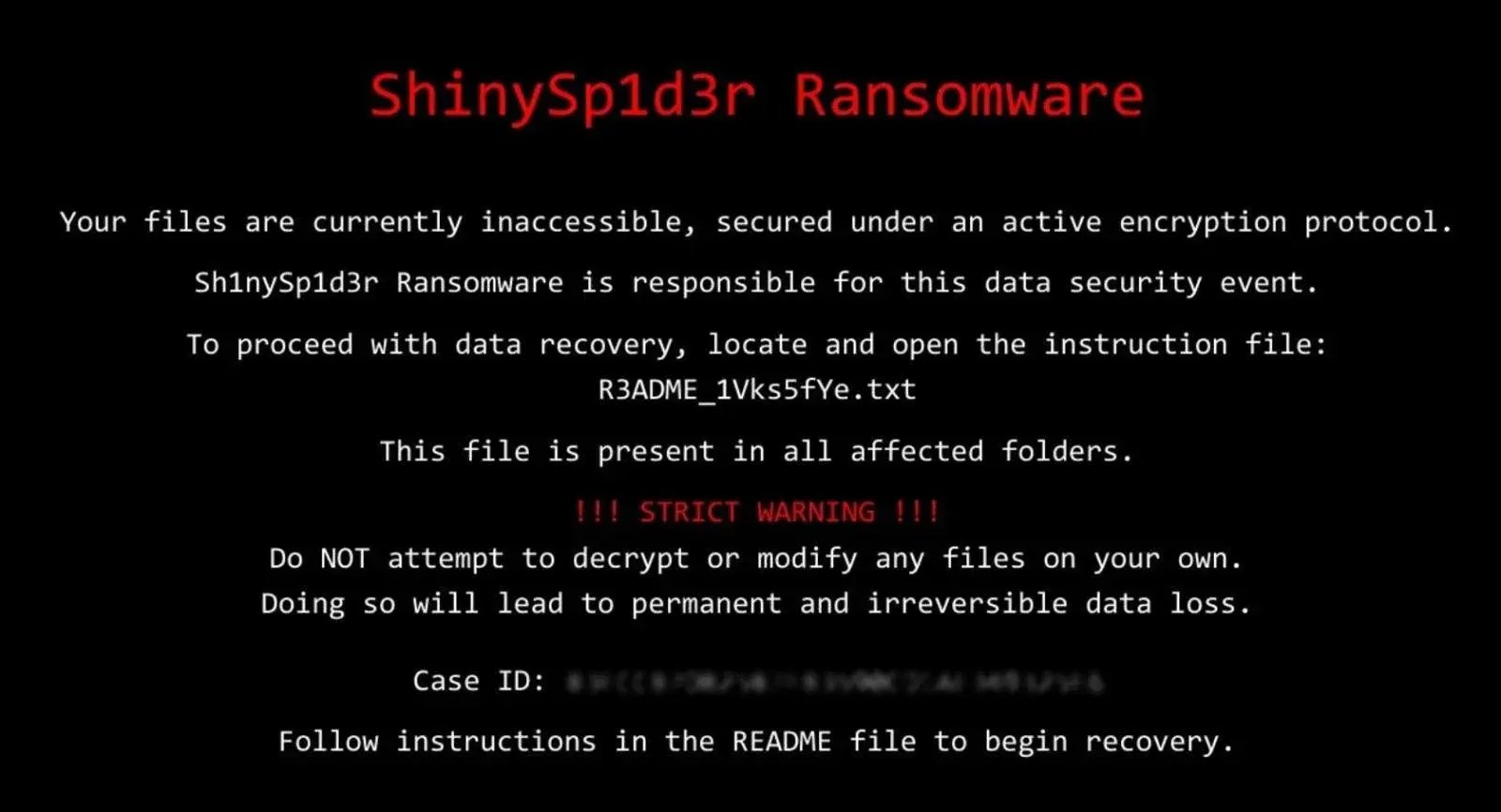
ShinySp1d3r Wallpaper (Source: BleepingComputer)
Read more: Ransomware 2025: Threats, Costs, and How to Defend Your Business
New Variants on the Way: Linux, ESXi, and More
For now, the available encryptor is focused on Windows systems, but the creators have already confirmed that versions for Linux and ESXi are nearly ready, which would significantly expand its reach. They also claim to have developed a command-line version with runtime configuration, making it easier to customize the attack based on the environment.
But that’s not all: the attackers are working on a special variant called “Lightning,” designed to be extremely fast. It’s written entirely in pure ASM (assembly language), which makes it lighter and harder to detect. According to them, this variant is similar to LockBit Green, another well-known ransomware family developed with a similar approach.
Since what’s been seen so far is just a test version in development, it’s highly likely that more features will be added in future releases.
Who’s Behind ShinySp1d3r?
All signs point to the full Ransomware-as-a-Service (RaaS) operation being managed by the ShinyHunters group, but it will operate under a new brand: Scattered LAPSUS$ Hunters (SLH). In fact, the name “ShinySp1d3r” appears to be a nod to the alliance between known groups like ShinyHunters, Scattered Spider, and LAPSUS$.
Are There Ethical Limits? The Group Says Yes, But…
The ransomware operators claim their encryptor will not be used to target organizations in the healthcare sector, including hospitals, clinics, pharmaceutical labs, and insurance companies. While this promise may sound reassuring, ransomware history shows that such claims are often broken. Other groups have made similar pledges in the past, only to completely disregard those “rules.”
They also state that affiliates are prohibited from attacking companies in Russia and the Commonwealth of Independent States (CIS), since many of the ransomware operators and collaborators are from that region, and targeting it could attract unwanted attention from local authorities.
How to Protect Against ShinySp1d3r Ransomware
At TecnetOne, we understand that ransomware is constantly evolving, which is why adopting a proactive, well-structured cybersecurity strategy is essential. Below is a practical guide with key measures to prevent and respond to threats like ShinySp1d3r:
-
Staff Training: Many attacks start with a simple phishing email. Training your team to recognize suspicious emails, malicious links, and dangerous attachments is one of the first lines of defense against ransomware.
-
Updated Backups: Having reliable backups, both in the cloud and offline, allows you to restore your systems without paying the ransom. It’s crucial to schedule automatic backups and regularly test their integrity. Solutions like TecnetProtect help automate backups, protect multiple environments, and verify data integrity, ensuring fast and effective recovery after any incident.
-
System and Software Updates: Keeping your operating systems, applications, and all security patches up to date significantly reduces vulnerabilities that attackers can exploit.
-
Strengthen Network Security: Implement firewalls, intrusion detection systems (IDS), and network segmentation to contain infections and prevent them from spreading within your infrastructure.
-
Zero Trust Model: Limit each user’s access only to the resources needed for their role. This “least privilege” principle minimizes risks in case an account is compromised.
-
Constant Monitoring: Continuously monitoring your systems and networks allows you to detect unusual behavior and respond immediately to potential threats. Proactive monitoring is key to containing an incident before it causes major damage.
What to Do in Case of an Incident
In addition to preventive measures, it’s important to maintain a strong security posture and be prepared to act if a ransomware attack occurs.
Conduct regular internal audits, vulnerability assessments, and penetration tests to spot weaknesses before attackers do. It's also essential to have a well-defined, tested incident response plan that outlines roles, procedures, communication channels, and recovery steps.
If an incident occurs, notify the appropriate authorities immediately, such as CERT teams, and seek professional cybersecurity support (like TecnetOne) to guide containment and recovery efforts.
Final Advice: Protecting against ransomware is not a one-time action but an ongoing strategy. ShinySp1d3r and other threats will continue to evolve, and your defenses must evolve with them.


