LockBit 5.0 emerged in late September 2025 and quickly caught the attention of cybersecurity experts. This version marks a significant leap for one of the world’s most notorious and dangerous ransomware-as-a-service (RaaS) groups.
What began in 2019 as the ABCD ransomware has evolved relentlessly. With each new version, LockBit has refined its arsenal—shifting tactics, adapting to defenses, and withstanding even the harshest blows from law enforcement and internal leaks.
Now, with LockBit 5.0, the group is taking its game to the next level. Built on the code of version 4.0, this new release introduces enhancements designed for more effective evasion and greater impact across corporate networks. In short: LockBit 5.0 isn’t just back—it’s stealthier, faster, and more dangerous than ever.
At TecnetOne, we help you understand this type of threat and show you how to protect your business before it’s too late.
What Does LockBit 5.0 Do? New Capabilities
Here are the main capabilities and features that set LockBit 5.0 apart:
a) Modular and Multi-Stage Architecture
LockBit 5.0 uses a two-stage execution model. In the first stage, a loader is activated to prepare the environment (persistence, evasion, etc.), and in the second stage, the actual payload is injected to encrypt data. For example, the loader creates a suspended “defrag.exe” process, injects it using ZwWriteProcessMemory, then resumes the thread to execute the payload in memory—bypassing security hooks and classic detections.
b) Cross-Platform Support: Windows, Linux, and VMware ESXi
One of LockBit 5.0’s most notable features is that it’s not limited to Windows systems. Samples exist for Linux and specifically for VMware ESXi—the widely used hypervisor in virtualized environments. This means attackers can take down not only workstations but also critical servers and virtual platforms, multiplying the operational impact.
c) Advanced Evasion and Anti-Analysis Techniques
LockBit 5.0 employs several techniques to make detection, analysis, and removal more difficult:
-
DLL reflection loading and heavy packing to hide the real payload.
-
Modification of the
EtwEventWritefunction (Event Tracing for Windows) to disrupt event logging used by many security tools. -
Termination of dozens of security services (up to 63 in some analyses).
-
Random 16-character extensions for encrypted files (e.g., “file.doc.xYzA9B4K12345678”), which complicates detection and automated recovery scripts.
-
Geolocation and language checks to avoid running on systems with Russian language settings or geolocated in Russia—a common trait among ransomware groups operating from that region.
d) Focus on Virtual Infrastructure and High Impact
The focus on VMware ESXi is especially concerning for companies running virtualized or cloud environments. By compromising an ESXi host, attackers can encrypt dozens or even hundreds of virtual machines at once, resulting in massive disruption.
e) Continued RaaS Business Model and Extortion Tactics
Like previous versions, LockBit 5.0 follows the ransomware-as-a-service model: ransomware developers provide tools (payload, control panel, infrastructure) to affiliates who carry out the attacks and share a cut of the ransom.
In version 5.0, affiliates must pay a deposit (around USD 500 in Bitcoin) to access the control panel—acting as an entry filter. The “double extortion” strategy remains: data encryption + data theft + public release if the ransom is not paid.
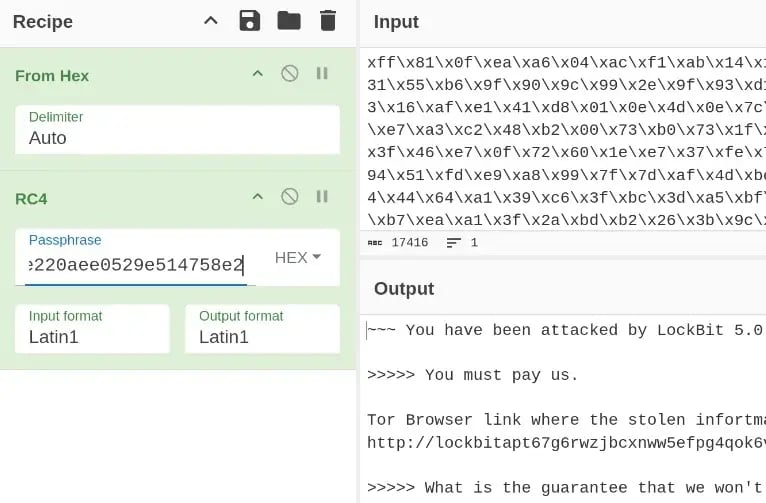
Ransom note decryption using RC4 (Source: FlashPoint)
Read more: LockBit 5.0 Ransomware: New Attacks on Windows, Linux, and ESXi
How Is LockBit 5.0 Different from Previous Versions?
- While earlier versions (such as LockBit 4.0) were already dangerous, LockBit 5.0 not only improves on the base code but also expands its reach to virtualized and cross-platform environments.
- It features a more flexible command-line interface, signaling greater refinement for affiliates operating these attacks.
- The modularity and code reuse lower the entry barrier for new affiliates—it’s more “plug-and-play.” This could increase the speed and volume of possible attacks.
- Improved encryption performance and faster propagation reduce the detection and containment window for defense teams.
In summary: this isn’t just a cosmetic or marketing update—it’s a real evolution that reinforces the threat.
Why Does This Matter?
LockBit 5.0 is not just another update—it poses a real risk to companies of all sizes and sectors. Its ability to target Windows, Linux, and virtualized environments like VMware ESXi makes it a threat capable of impacting every layer of modern IT infrastructure.
In Mexico, the U.S., and across Latin America, many organizations operate in hybrid and virtualized environments, making them especially vulnerable. A single compromised server can encrypt multiple virtual machines and bring critical operations to a halt in minutes.
Moreover, the traditional “detect and respond” approach is no longer enough. LockBit 5.0 drastically reduces the reaction window, forcing companies to strengthen their prevention strategies, network segmentation, immutable backups, and solid disaster recovery plans.
The reality is that many businesses still have gaps in remote access protection, hypervisor management, or backup security. These are precisely the weaknesses LockBit 5.0 exploits to cause maximum damage. Being prepared is not optional—it’s the only way to ensure operational continuity in the face of such threats.
Best Practices to Protect Against LockBit 5.0
At TecnetOne, we know that facing threats like LockBit 5.0 takes much more than a simple antivirus solution. This type of ransomware demands a comprehensive strategy that combines prevention, detection, response, and recovery.
That’s why we’re sharing some best practices you can implement (and that are part of our SOC, XDR, backup, and awareness solutions) to strengthen your infrastructure security and keep your operations safe.
Prevention: The Best Defense Is Being Proactive
-
Update everything without delay. Keep your operating systems, hypervisors (like VMware ESXi), virtualization software, and critical applications up to date. LockBit 5.0 often exploits vulnerabilities in outdated environments.
-
Segment your network. Separate critical areas (like servers or hypervisors) from the rest of the network and apply the principle of least privilege for admin accounts.
-
Enable multi-factor authentication (MFA). Use phishing-resistant methods like security keys or FIDO2 standards. This makes it harder for attackers to access systems with stolen credentials.
-
Harden security in virtual environments. Enable lockdown mode on ESXi, limit shell or admin interface access, monitor configuration changes, and use internal firewalls.
-
Train your team. At TecnetOne, we promote cybersecurity awareness programs that teach how to spot phishing attempts, manage passwords, and apply backup best practices.
Detection and Response: Spot and React Quickly
-
Deploy EDR or XDR solutions. These tools detect anomalous behavior on workstations, Linux servers, hypervisors, and containers—covering the entire environment.
-
Detect in-memory attacks. LockBit 5.0 uses techniques like DLL reflection or process hollowing to evade traditional signatures. A modern XDR can identify these patterns in real time.
-
Monitor your infrastructure. Watch for unusual hypervisor access, virtual disk (VMDK) changes, or abnormal data transfers. Exfiltration often precedes encryption.
-
Run simulations. Conduct ransomware tabletop exercises to evaluate how your organization would respond to a real attack—detection time, internal communication, and recovery.
Recovery and Resilience: Be Ready to Bounce Back Fast
-
Create offline and immutable backups. Ensure your backups are beyond ransomware’s reach—disconnected or protected with immutability technologies. With TecnetProtect, you can automate this process and keep your backups safe in the cloud or on-prem, with advanced protection against unauthorized modification or encryption. This guarantees your data is always available for fast, reliable restoration—even after a ransomware attack.
-
Test your restores. Having backups isn’t enough—you must ensure they can be restored without errors.
-
Design business continuity plans. Include scenarios involving mass encryption, hypervisor loss, or total virtualization outages.
-
Isolate backup systems. Use recovery tools outside the main network to prevent LockBit from reaching your backup copies.
At TecnetOne, we understand that cybersecurity isn’t just about reacting—it’s about anticipating. Our comprehensive cybersecurity solutions are designed to help you detect, contain, and recover from threats like LockBit 5.0.
Protecting your business doesn’t have to be complicated: with the right strategy and tools, you can keep your infrastructure secure and operational—even in the face of the most sophisticated attacks.


