For years, digital identity was relatively straightforward. You knew where it lived, how it was managed, and who had access. Everything was centralized in an LDAP directory, an HR system, or an identity and access management (IAM) portal. If you needed to know who was who within your organization, that’s where you’d look.
Today, that world is gone.
If you manage a modern company or work in IT or cybersecurity, you’re now dealing with a fragmented, distributed, and largely invisible identity landscape. This hidden layer of identities—unseen, unmanaged, and uncontrolled—is what we call Identity Dark Matter. At TecnetOne, we believe understanding it is key to securing your digital environment.
Identity No Longer Lives in One Place
Digital transformation has reshaped how identities are created and used. In your organization today, you likely have identities spread across:
- SaaS applications
- On-premise systems
- Cloud infrastructure (IaaS and PaaS)
- Internally developed apps
- Unauthorized tools (shadow IT)
Each of these has its own users, credentials, permissions, and authentication flows. But traditional IAM/IGA systems only govern the documented and integrated parts. Everything else falls outside their reach.
That’s where Identity Dark Matter lives: identities that operate with access rights but are invisible to governance.
The Hidden Cost of Identity Integration
Every new app requires a complex onboarding process: connectors, schema mapping, role definitions, and more. It’s costly and resource-heavy. Many apps never complete that process.
This results in fragmented identity management, with users and permissions functioning outside official controls—not because someone intended it, but because IAM models can’t keep up with business velocity.
Read more: Trump and the Digital War: Why Outsourcing Cybersecurity Is Dangerous
The Bigger Issue: Non-Human Identities (NHI)
Human identities are already hard to manage. But non-human identities multiply the problem.
This includes:
- APIs
- Bots
- Service accounts
- Automated processes
- AI agents
These identities authenticate, interact, and execute critical actions. Yet often:
- They’re created for temporary projects
- Have no clear owner
- Aren’t part of a defined lifecycle
- Go unreviewed and unremoved
Even in “managed” apps, these entities may operate without oversight. And IAM systems were never built to handle them.
This is the deepest—and riskiest—layer of Identity Dark Matter.
What Makes Up Identity Dark Matter?
As your org evolves, identity sprawl falls into several high-risk categories:
- Shadow apps: Tools that run outside governance because integrating them is too slow or costly—but still process data and access.
- Non-human identities: APIs, bots, and service accounts with unchecked autonomy.
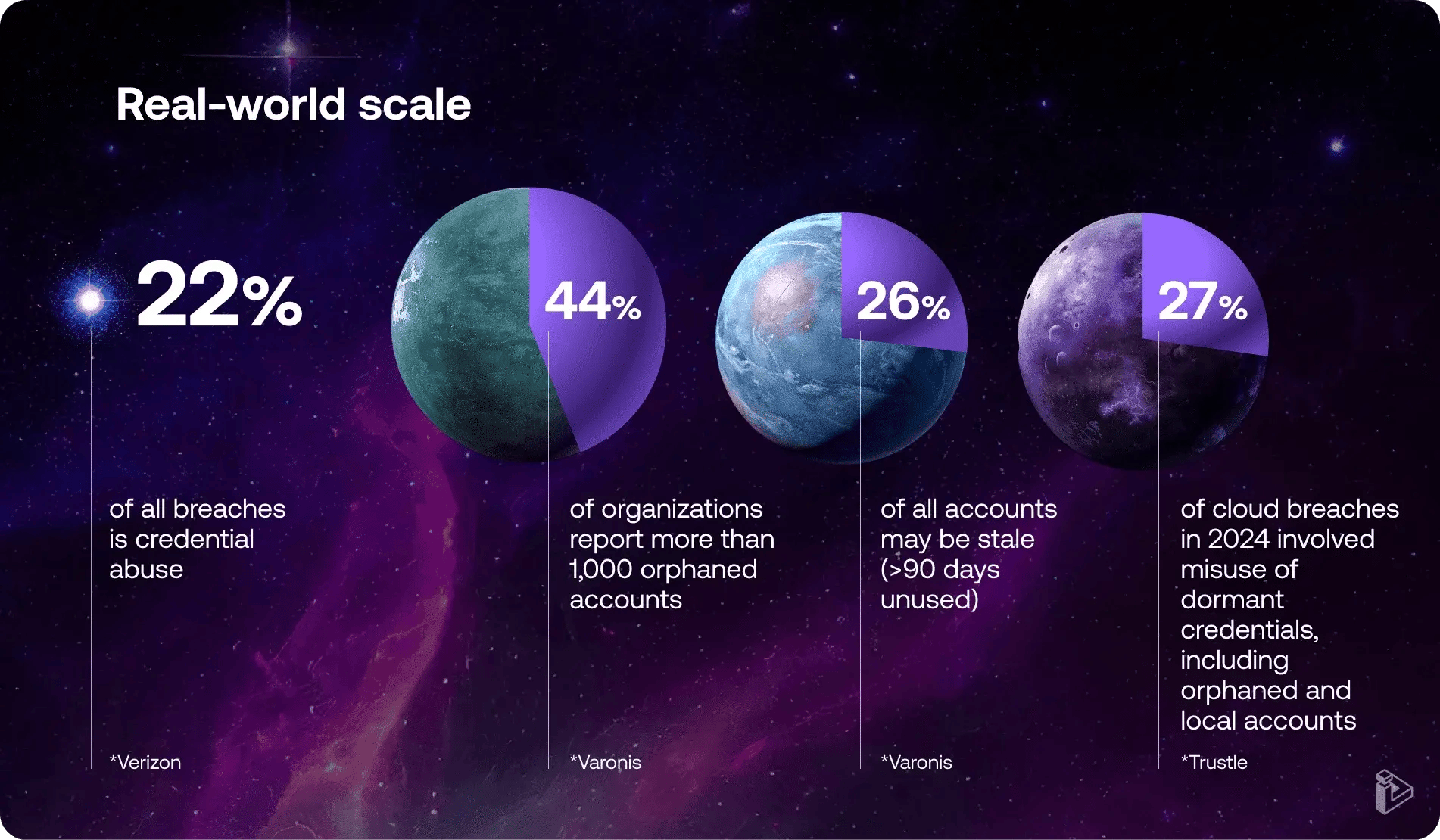
- Orphaned and stale accounts: 44% of orgs admit to 1,000+ orphaned accounts; 26% of accounts inactive for 90+ days.
- AI agents: Autonomous systems making decisions and granting access outside traditional models.
Why Identity Dark Matter Is a Security Crisis
These invisible identities create blind spots where risk thrives. This isn’t hypothetical: in 2024, 27% of cloud breaches involved stale, orphaned, or local credentials.
Top risks include:
- Credential abuse: 22% of breaches involve valid credential misuse. No hacking needed—just log in.
- Lack of visibility: You can’t protect what you don’t see. Many orgs live with a false sense of control.
- Compliance & incident response delays: Unmanaged identities fall outside audit scopes and slow down investigations.
- Lateral movement & internal threats: These hidden identities enable silent privilege escalation.
(Source: The Hacker News)
The Mistake: Thinking Configuration = Control
Most orgs rely on configuring IAM systems and assume that equates to identity governance. But in a fragmented world, configuration alone fails.
At TecnetOne, we believe identity security must shift from configuration to observability.
The Shift: Identity Observability
Solving Identity Dark Matter requires a new approach: Identity Observability—continuous, evidence-based visibility over all identities, human and non-human.
It’s based on three pillars:
- See Everything
Collect telemetry from all apps—not just those with IAM connectors. - Prove Everything
Build unified traceability: who accessed what, when, and why. No assumptions—just proof. - Govern Everywhere
Apply controls across managed, unmanaged, and AI-driven identities—no exceptions.
When you unify telemetry, auditing, and orchestration, Identity Dark Matter becomes actionable insight.
You might also be interested in: Coatlicue: Supercomputer Without Digital Foundations in Mexico
What This Means for Your Business
To reduce real-world risk, accept a hard truth: your identity perimeter is much bigger than you think.
You must:
- Detect forgotten identities
- Monitor automated access
- Review inactive accounts
- Understand how AI agents behave
Governance can’t be based on declarations—it must be grounded in evidence.
The TecnetOne Vision
At TecnetOne, we believe the future of cybersecurity lies in making the invisible visible. Identity must be managed like modern observability: understanding how it’s created, used, and behaves in real time.
Only then can you ensure that security and compliance aren’t promises—they’re provable outcomes.
Conclusion: The Most Dangerous Risk Is the One You Don’t See
Identity Dark Matter isn’t a buzzword—it’s a reflection of how business, tech, and threats have evolved.
If ignored, these invisible identities will keep operating in the background, silently expanding your attack surface.
The good news? It can be fixed. But it starts by accepting that half your identity universe may be hiding in plain sight. And recovering that visibility is no longer optional—it’s a baseline requirement for digital survival.


